WannaCry - Detail Analysis and Remediation
Hisham Mir
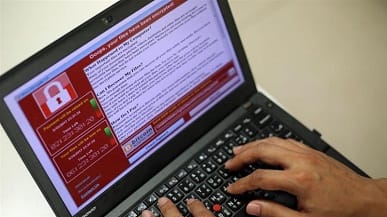
WannaCry is now a hot topic in cyber world as it is been reported in more than 150 countries around the globe, affecting thousands of machines and many companies with its encryption. News came to circle when National Health Service (NHS) was under attack of WannaCry where it infected almost all National Health Service machines but steadily it spread into other parts of country and then into other continents. So a question arise how this all happened? The ransomware was first seen on Friday and spread rapidly through numerous substantial associations around the world. Not at all like earlier ransomware, this specimen utilized the SMBv1 "ETERNALBLUE" adventure to spread. "ETERNALBLUE" wound up noticeably open about a month back when it was featured by Shadowbroker part of NSA hacking tools. Before going into detail, lets see how WannaCry work and how it can effect you.
How WannaCry work & how it can Infect You
According to FBI Alert the WannaCry ransomware start its infection by different campaign or a compromised network or RDP, now once this ransomware gets into any network it start spreading into network further due to its worm capabilities. Some organizations suggest that the initial infection originated from e-mail attachments, but little is known about the e-mails. It is easily possible that other malware was confused with WannaCry, Others suggested that affected organizations may have had vulnerable systems exposed via port 445. Up to now, affected organizations have not shared a lot of proof to show how the initial infection happened but these two mediums can be used easily.
After working on WannaCry we concluded that 2 types of keys are deployed which is tact of normal worms. One key is assigned to encrypt and 2nd is used to encrypt other files to show victim some demo to show what they have done with victim files. So this help the worm to generate new RSA key for each infected user. We have seen on social media that people claimed to have a decryption password (WNcry@2ol7) which may work on all but it is wrong and wont work as WNcry@2ol7 is just used to decrypt some functions of it.
After WannaCry attack on victim machine it ecrypt machine files into an ecryption extension .wncry. To decrypt the files, the user is asked to pay $300, which will increase to $600 after a few days. The ransomware threatens to delete all files after a week if victim didn't paid the amount. The most important and tricky part is WannaCry also installs a DOUBLEPULSAR (also part of the NSA tools leak)backdoor. The backdoor could be used to compromise the system further and will also install Tor browser to facilitate communication with the ransomware owners easily and securely.
How to know if you are infected?
- Systems that are infected by WannaCry will try to connect to a specific domain. Encrypted files will have the “wncry” extension.
- Systems will scan internally for port 445
- Ransom message will be displayed
- In addition, infected systems will reach out to sites for crypto keys
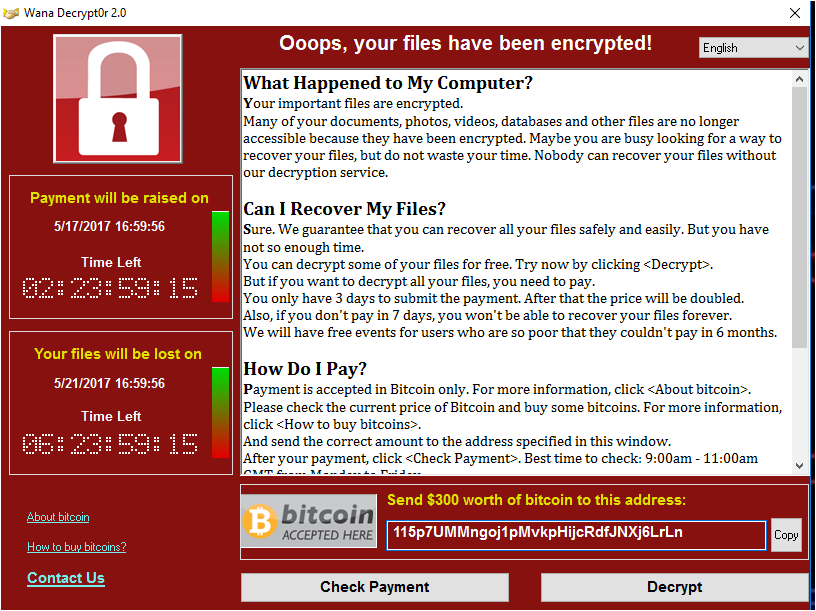
WannaCry Infection Stats
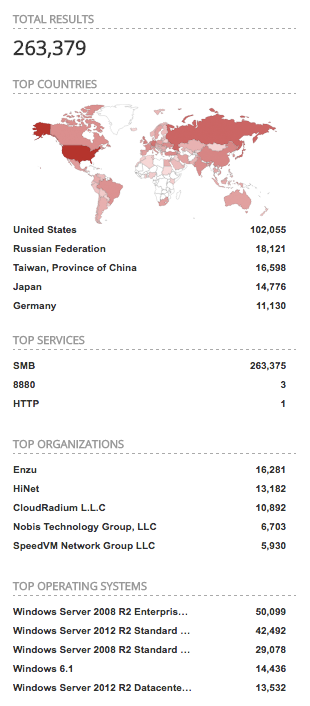
WannaCry HeatMap By Symantec
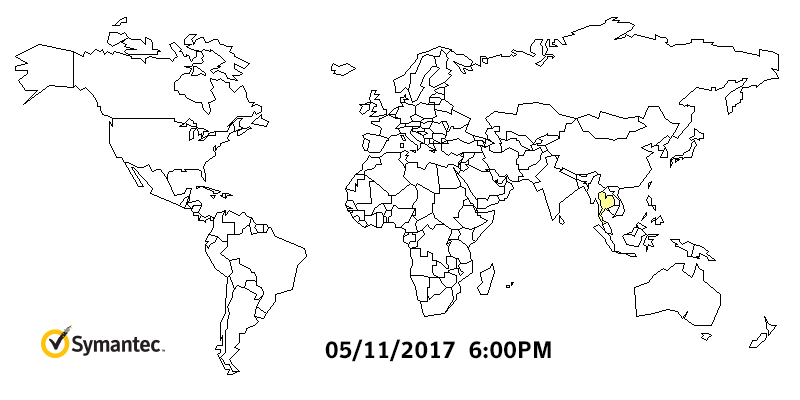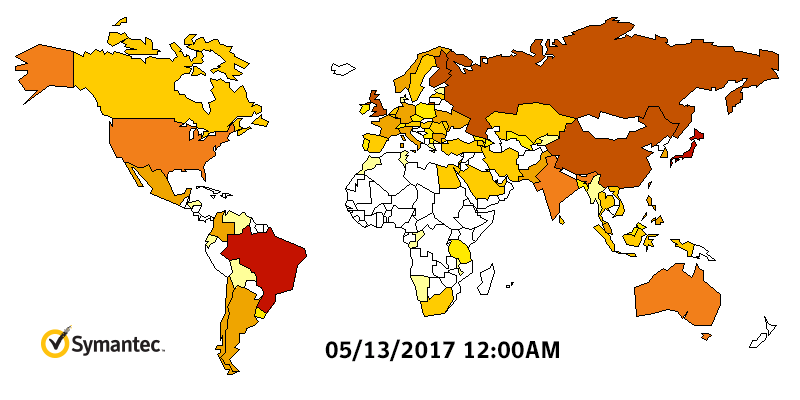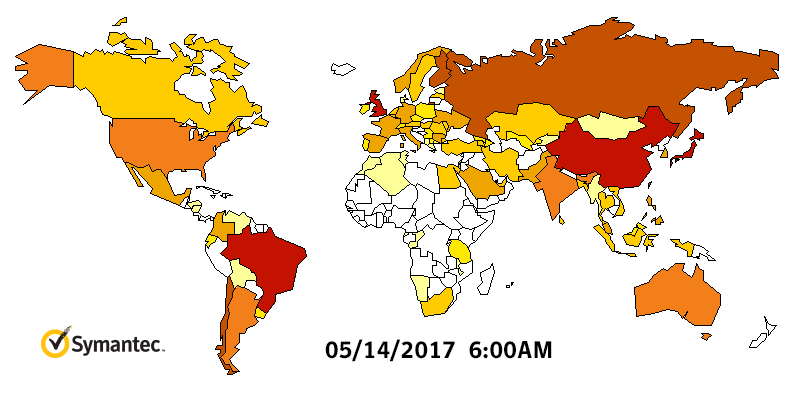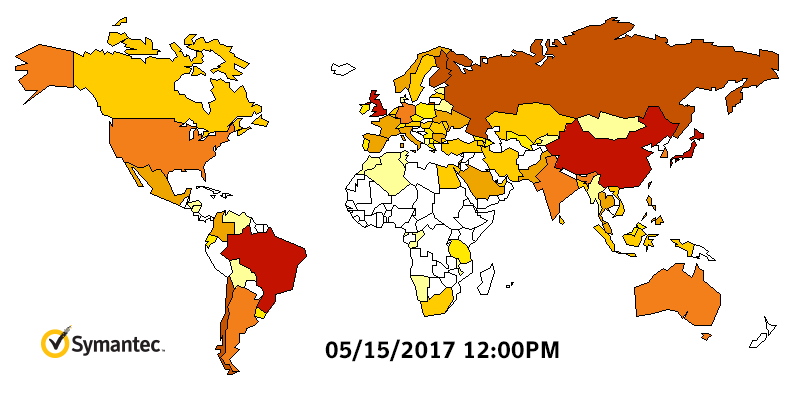
What if you are infected
Well Seriously there is no simple solution to tackle this ransomware but if you have backup files wipe affected machines but make sure you installed updates once you get live with backup, Second choice is paying the ransom, but it depend on how important the encrypted data is and till now there is no report from victims who paid the ransom and got decryption password.
Remidation
- MS17-010 is a known and infected which was fixed by Microsoft in March 2017. Also, Microsoft made fix for its other OS, including Windows XP, Windows 8, and Windows Server 2003.
- For the present, the best exhortation is to refresh your antivirus on endpoints, to guarantee that all Windows frameworks are completely fixed, to design firewalls to square access to SMB and RDP ports, and to teach clients to keep an eye out for suspicious messages.
- It's striking that WannaCry introduces the DOUBLEPULSAR on to infected machine. This is a piece mode payload which can subjectively infuse DLLs into user.
- Enable your machine Firewall and keep eye on your ports traffic
- Don't open any kind of Suspicious Emails or download suspicious file from any un-trusted Websites
- Disable Server Message Block (SMBv1) protocol
This post is to aware normal users, system administrators, DataCenter, etc. We are coming up with full technical analysis in coming days with more details.