What Is PTaaS? Penetration Testing as a Service Explained (2026 Buyer's Guide)
Hisham Mir
January 7, 2026

What Is PTaaS?
PTaaS (Penetration Testing as a Service) is a subscription-based model that replaces one-off penetration tests with continuous, platform-driven security testing. Instead of waiting months for a static PDF report, security teams get real-time vulnerability findings, on-demand access to human testers, and built-in remediation workflows — all through a cloud platform.
In plain terms: PTaaS turns penetration testing from a yearly audit event into an always-on security capability.
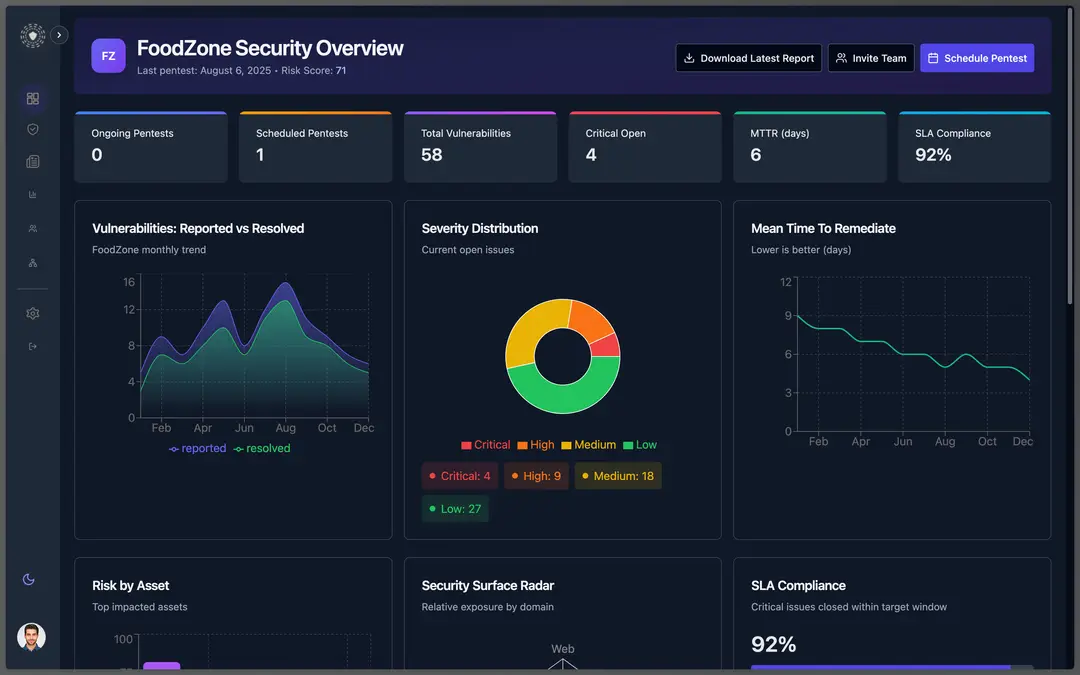
Table of Contents
- Why Traditional Pentesting Fails Modern Teams
- PTaaS Meaning: What It Is and How It Works
- PTaaS vs Annual Pentest: Key Differences
- How to Evaluate PTaaS Platforms: A Buyer's Checklist
- What to Watch Out For
- How SLASH Extends PTaaS into Hybrid Offensive Security
- Bottom Line: Is PTaaS Right for You?
Why Traditional Pentesting Fails Modern Teams
The traditional penetration testing model was designed for a slower era:
- Scope is defined months before testing begins
- Testing happens once or twice a year
- Findings arrive as a static PDF
- Retesting is slow, expensive, or simply skipped
This model breaks under modern conditions. Engineering teams deploy daily. Infrastructure is cloud-native, API-driven, and constantly changing. A vulnerability introduced three weeks after an annual pentest sits invisible until the next cycle unless something goes wrong first.
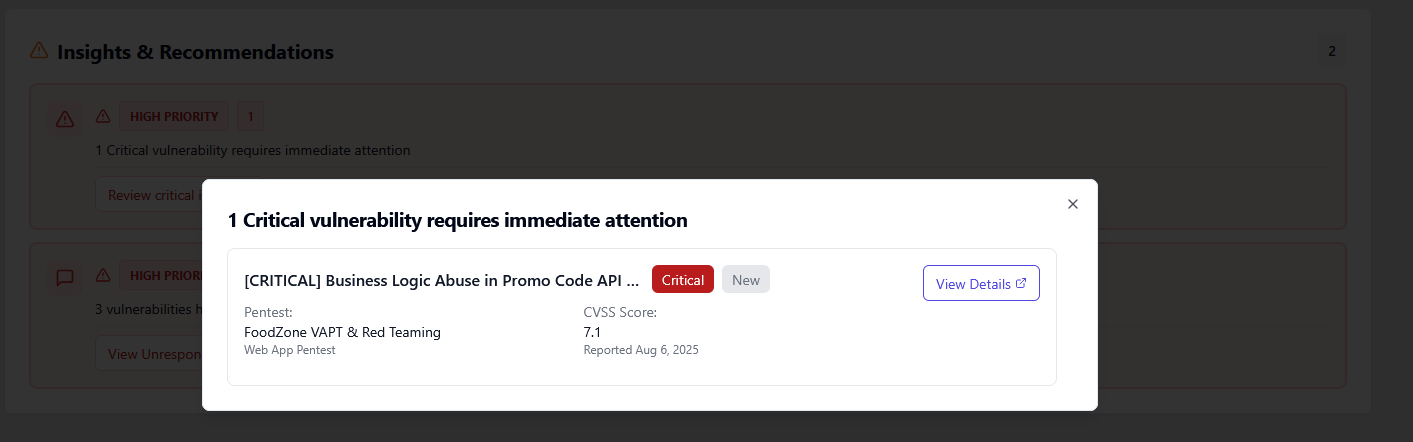
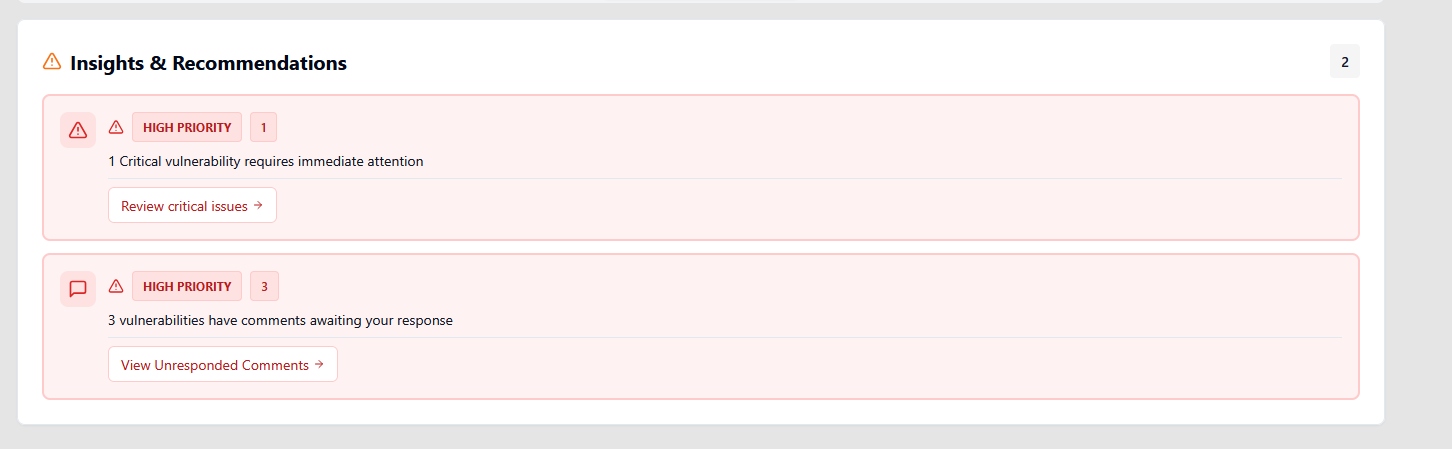
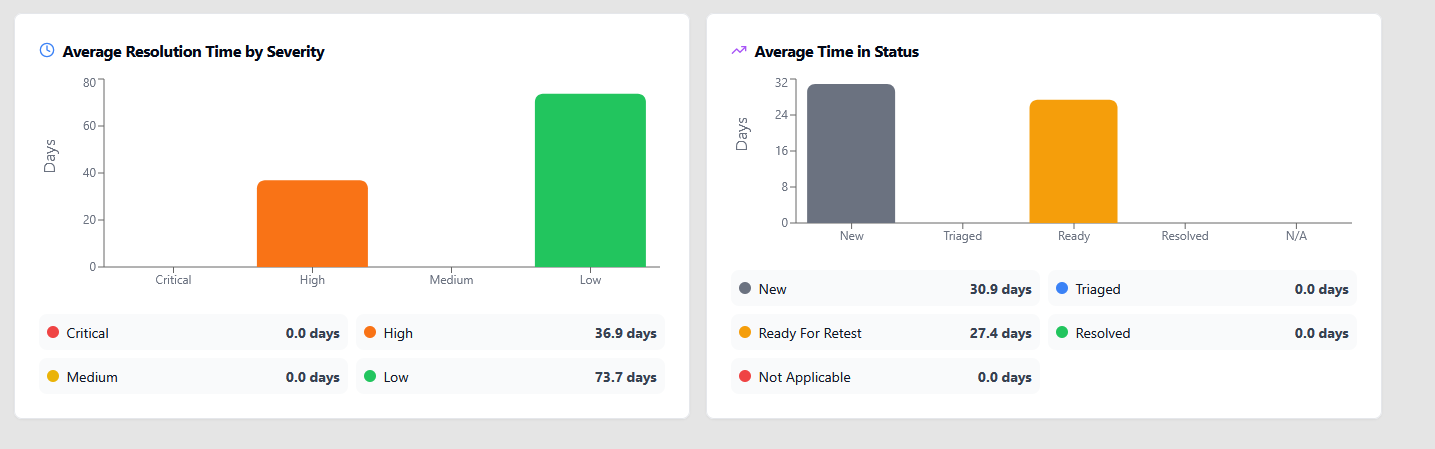
The result is a dangerous gap: executives feel assured based on outdated results, while security leaders struggle to explain how "we passed the pentest" didn't prevent the incident.
The problem isn't the testers. It's the delivery model.
PTaaS Meaning: What It Is and How It Works
PTaaS replaces point-in-time engagements with a continuous testing loop built on three pillars:
1. A Live Platform (Not a PDF)
The PTaaS platform centralizes everything: asset scopes, engagement scheduling, vulnerability tracking, evidence, exploit details, and retesting status. Unlike a static report, the platform stays alive updating as new findings appear and issues are resolved.
2. Human-Led Testing (Not Just Scanners)
A common misconception is that PTaaS equals automated scanning. Credible PTaaS platforms rely on human testers to chain vulnerabilities, bypass business logic, and identify real-world exploit paths. Automation supports scale. Humans deliver signal.
3. Continuous Reporting and Collaboration
Instead of a final report delivered weeks after testing ends, PTaaS surfaces findings as they're discovered with reproduction steps, business impact context, and built-in retesting once fixes are deployed. Security and engineering teams work from the same platform in real time.
PTaaS vs Annual Pentest: Key Differences
This is the question most buyers are really asking when they search "what is PTaaS."
| Area | Annual Pentest | PTaaS | ⚡ SLASH — SecurityWall |
|---|---|---|---|
| Testing Frequency | Once or twice a year | Continuous or recurring | Always-on |
| Scope Flexibility | Fixed at project start | Adjustable per engagement | Continuously aligned to real exposure |
| Speed of Findings | Final report after weeks | Faster, still engagement-based | Near real-time |
| Testing Approach | Mostly manual | Human-led + limited automation | Human + machine orchestration |
| External Exposure Visibility | ✕ Not covered | ◑ Limited | Global exposure intelligence (VIGIX) |
| Reporting Format | PDF only | Platform + PDF | Live platform + PDF + certification |
| Retesting Fixes | ✕ New contract required | ◑ Scheduled retesting | ✓ Immediate validation |
| Remediation Support | ✕ Minimal | ◑ Collaborative | ✓ Integrated with dev workflows |
| Executive Reporting | Historical PDF | Dashboard + trends | Live risk posture + audit-ready certs |
|
Ready to move beyond annual audits?
Explore the SLASH Platform — SecurityWall's PTaaS Solution →
|
|||
The short version: An annual pentest tells you where you stood months ago. PTaaS tells you where you stand now.
How to Evaluate PTaaS Platforms: A Buyer's Checklist
If you're actively evaluating PTaaS vendors, these are the five capabilities that separate credible platforms from rebranded scanner services.
1. Continuous Asset Discovery (Not Just Declared Scope)
Static scopes break instantly in modern environments. Subnets change, subdomains are spun up, cloud resources appear without documentation. A mature PTaaS platform must continuously discover your attacker-visible attack surface not just test the assets you remembered to list.
Ask vendors: How does your platform handle assets added after scope is defined? Do you track shadow IT or unmanaged exposure?
2. Human Testers, Not Just Tool Runs
Automated scanners catch known CVEs. They don't catch business logic flaws, API abuse chains, or the creative lateral movement paths that real attackers use. Confirm that human experts are actively involved in testing not just reviewing automated output.
Ask vendors: Who performs the testing? Can I see tester credentials? How are findings validated before they're surfaced?
3. Real-Time Findings, Not Batch Reports
If findings only surface in a final report after the engagement closes, you're still on a delayed feedback loop. Real PTaaS delivers findings as they are discovered, so teams can begin remediation while testing is still active.
Ask vendors: When are findings surfaced? Can my engineering team see and act on vulnerabilities before the engagement ends?
4. Integrated Retesting Without New Contracts
Remediation without retesting is incomplete. If every retest requires a new statement of work, the cost and friction will cause teams to skip validation. Look for platforms that include retesting as part of the subscription.
Ask vendors: How is retesting handled? Is it included, or does it require a new engagement?
5. Executive-Ready Reporting and Audit Trail
Security leaders need to communicate risk to boards and auditors not just engineering teams. Look for platforms that provide live risk dashboards, trend data over time, and exportable reports suitable for compliance or certification purposes.
Ask vendors: What does executive reporting look like? Can outputs be used to satisfy compliance requirements (SOC 2, ISO 27001, etc.)?
What to Watch Out For
Not every "PTaaS" offering delivers what the label implies. Common red flags:
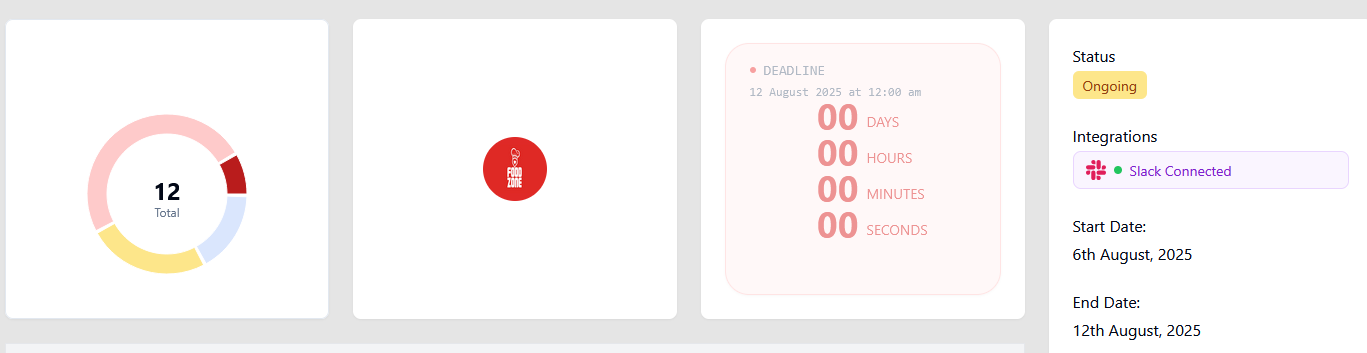
- Automation-only platforms rebranded as PTaaS no real human testing involved
- Batch reporting disguised as continuous delivery (findings still arrive in a final PDF)
- Rigid scopes that don't accommodate environments that change frequently
- No retesting included — remediation validation requires a new paid engagement
- No external exposure layer — the platform only tests what you tell it to, missing attacker-visible assets you don't know about
How SLASH Extends PTaaS into Hybrid Offensive Security
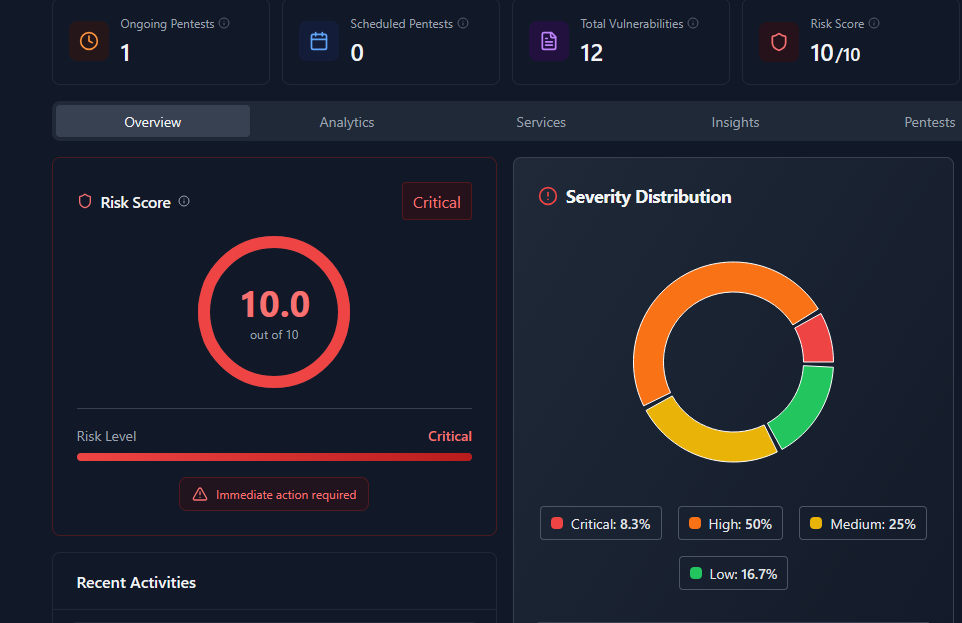
Most PTaaS platforms improve how penetration testing is delivered. SLASH goes a step further: it operationalizes offensive security as a continuous system, not a recurring engagement.
Here's what makes SLASH different:
Near real-time findings. SLASH surfaces vulnerabilities as testing happens not after a post-engagement review window. Security and engineering teams can act immediately rather than waiting for a report to close.
Machine + human testing in combination. SLASH combines automated machine-driven testing (continuous, scalable, running across infrastructure as it changes) with human-led expert testing (business logic, chained exploits, multi-path attack simulation). Neither alone is sufficient. Together, they reflect how real attacks actually unfold.
VIGIX: Global Exposure Intelligence. What makes SLASH structurally different from conventional PTaaS is the VIGIX layer a global exposure and intelligence engine that provides:
- Attacker-view visibility of your internet-facing assets
- Detection of misconfigurations and shadow infrastructure
- Dark web monitoring for data exposure and credential leaks
- Real-world threat intelligence on emerging attacker behavior
This means testing isn't performed against a declared list. It's performed against your actual exposure what an attacker sees when they look at your organization from the outside.
The practical result: Findings from SLASH are not theoretical or tool-generated guesses. They are discovered at scale, validated by real testers, and contextualized with real-world exposure data. SLASH doesn't just surface what is vulnerable it shows why it matters, how it could be attacked, and where to act first.
Is PTaaS Right for You?
If any of these describe your situation, PTaaS is worth a serious evaluation:
- Your engineering team deploys frequently, but security testing happens once or twice a year
- You've had a finding show up in production that should have been caught earlier
- Your current pentest reports sit in a folder and aren't driving active remediation
- You need to demonstrate ongoing security assurance to auditors, customers, or your board
- You're tired of paying for new engagements every time you want to retest a fix
Why PTaaS Matters Now
If you’re searching “what is PTaaS”, chances are you’re already feeling the limitations of traditional security testing.
PTaaS matters because:
- Attackers don’t wait for annual assessments
- Software changes daily
- Risk needs to be managed continuously not reported retroactively
PTaaS isn’t just a new delivery model. It’s a response to how modern organizations actually operate. PTaaS transforms penetration testing from a periodic audit into an always-on security capability. For organizations serious about reducing real-world risk, it’s no longer optional it’s foundational.
And platforms like SLASH show where PTaaS is headed next with innovation.
Annual penetration tests aren't wrong they're just insufficient on their own. PTaaS closes the gap between when vulnerabilities are introduced and when they're discovered. For organizations operating in modern environments, that gap is where breaches happen.
PTaaS transforms penetration testing from a periodic audit into an always-on security capability. For organizations serious about reducing real-world risk, it's no longer a nice-to-have. It's foundational.
SecurityWall's SLASH platform is built on the PTaaS model extended with global exposure intelligence, human-led testing, and near real-time findings. Book a call to see how it works in practice.
Tags
About Hisham Mir
Hisham Mir is a cybersecurity professional with 10+ years of hands-on experience and Co-Founder & CTO of SecurityWall. He leads real-world penetration testing and vulnerability research, and is an experienced bug bounty hunter.