SOC Monitoring & Management: What to Monitor (and What Not To)
Hamza Razzaq
January 27, 2026

What SOC Monitoring and Management Really Is
SOC monitoring is the continuous process of collecting, analysing, and responding to security events across an organisation's infrastructure. A SOC (Security Operations Center) monitors logs, alerts, and threat intelligence 24/7 to detect and contain incidents before they cause damage.
SOC monitoring is frequently described as the act of collecting logs, generating alerts, and watching dashboards. While that definition is technically correct, it misses the operational purpose of a security operations center.
The real goal of SOC monitoring is not visibility it is decision support. Monitoring should help security teams quickly determine whether something represents real risk, what impact it could have, and what action should be taken next.
SOC monitoring and management go hand in hand. Monitoring provides the raw signals. Management provides prioritization, investigation workflows, response coordination, and continuous improvement. Without management, monitoring becomes noise. Without monitoring, management has nothing to act on.
For a broader overview of how Security Operations Centers are structured and why they exist, see our Security Operations Center (SOC) Guide.
Most SOC challenges emerge when these two functions drift apart.
How Traditional SOC Monitoring Shows Up in Practice
In most organizations, SOC monitoring evolved organically over time.
New tools were added. New environments were connected. New compliance requirements appeared. Each change brought more logs, more alerts, and more dashboards often without removing anything that came before.
As a result, traditional SOC monitoring typically includes:
- Network telemetry from firewalls and IDS systems
- Endpoint activity from EDR tools
- Authentication and identity logs
- Cloud platform and SaaS audit logs
- Application and infrastructure telemetry
Individually, these data sources are valuable. Collectively, they often overwhelm SOC teams.
The most common outcome is a SOC that is extremely busy but not necessarily effective analysts spend most of their time triaging alerts instead of investigating threats, and real incidents are detected late or missed entirely.
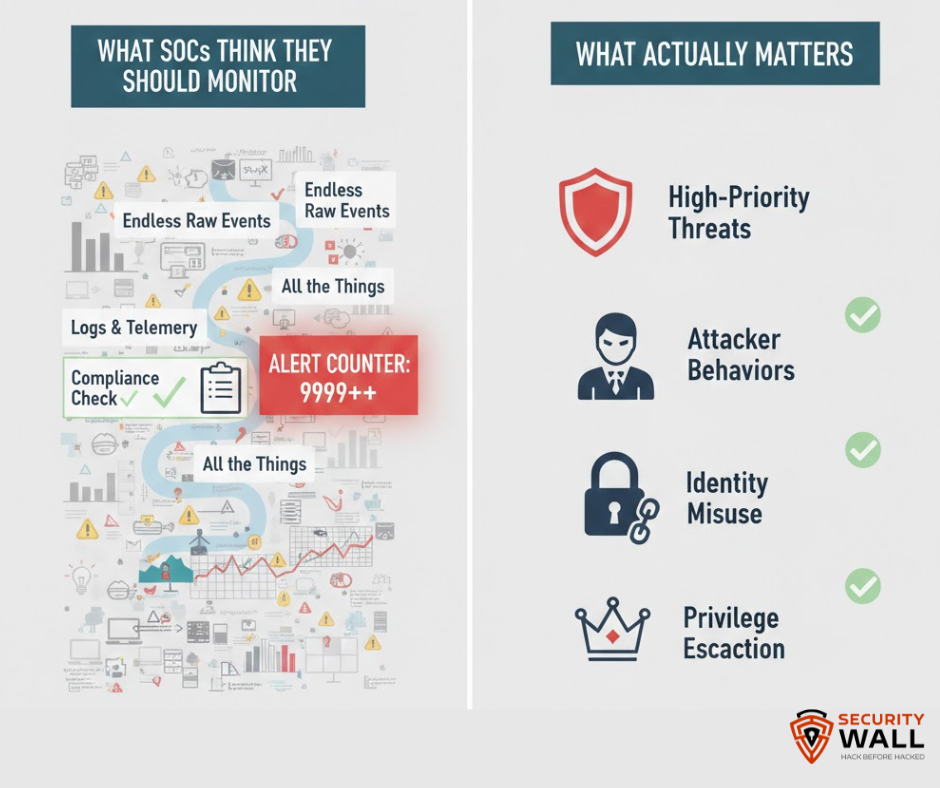
What SOC Teams Think They Should Monitor (But Shouldn’t)
Most SOC monitoring problems are rooted in assumptions that sound reasonable but don’t hold up in practice.
The “Collect Everything” Mentality
Many SOCs operate under the belief that collecting more data automatically improves security. This leads to indiscriminate log ingestion across every system, service, and application.
In reality, excessive data collection creates three major problems:
- Noise amplification – Low-risk events dominate alert queues.
- Operational cost – Storage, licensing, and processing costs grow rapidly.
- Cognitive overload – Analysts struggle to distinguish meaningful signals from background activity.
Collecting everything does not improve detection. It dilutes it.
Talk to a Security Operations Center (SOC) Expert
Before a Hacker Breach Happens
Low-Fidelity Alerts With No Investigative Value
Another common issue is alerts that trigger on single events without context.
Examples include:
- A failed login alert with no user history
- A malware alert with no execution or persistence indicators
- A policy violation alert with no defined response action
Alerts like these provide activity but not insight. Over time, analysts learn that most alerts can be safely ignored a dangerous habit that attackers exploit.
Alert fatigue is not caused by analysts missing alerts. It is caused by alerts that never should have existed.
Compliance-Driven Monitoring That Obscures Detection
Compliance requirements often mandate extensive logging, and those requirements are valid. Problems arise when compliance monitoring becomes the foundation of SOC detection strategy.
Compliance logs are designed to answer audit questions, not attack questions. When SOCs treat compliance visibility as detection coverage, they flood analysts with data that rarely indicates real threats.
Mature SOCs separate compliance monitoring from threat detection, even when they use the same underlying data sources.
As monitoring environments grow more complex, many SOC teams turn to Automation and AI to reduce manual triage and improve detection quality. Automation helps enrich alerts, reduce noise, and accelerate response when built on a solid monitoring foundation.
What Actually Matters: High-Signal SOC Monitoring
High-performing SOCs do not monitor less they monitor smarter.
They focus on signals that indicate attacker behavior, risk escalation, and potential impact.
Monitor Behaviors, Not Isolated Events
Attackers do not operate in single log entries. They operate through sequences of actions.
Effective SOC monitoring looks for:
- Authentication anomalies followed by privilege changes
- Lateral movement across systems
- Suspicious command execution tied to persistence
- Cloud API usage that deviates from normal administrative behavior
This behavioral focus is where proactive capabilities like threat hunting add value.
Detection quality improves dramatically when SOC monitoring is designed around attacker workflows instead of individual alerts.
Not sure if your SOC is monitoring the right things?
Logs and Signals SOC Teams Should Prioritize
Not all logs contribute equally to detection. High-signal SOC monitoring consistently prioritizes:
- Authentication and identity misuse – anomalous logins, impossible travel, token abuse
- Privilege escalation – role changes, admin access grants, permission abuse
- Lateral movement indicators – credential reuse, remote execution, service creation
- Command execution and persistence – scheduled tasks, startup scripts, registry changes
- Cloud control-plane activity – API abuse, role assumption, infrastructure manipulation
- Security control tampering – disabled agents, logging suppression, policy changes
These signals align closely with attacker objectives the same behaviors exercised during red team operations.
Context Is the Difference Between Noise and Signal
The same alert can be harmless or critical depending on context.

High-signal SOC monitoring enriches detections with:
- Asset criticality
- User privilege level
- Historical behavior patterns
- Threat intelligence
A failed login on a test account is routine.
The same failure on a privileged cloud administrator account at an unusual time is an incident.
Context transforms alerts into decisions.
Common SOC Monitoring Mistakes That Cause Alert Fatigue
Alert fatigue is not inevitable. It is the result of design choices.
Alerts With No Ownership or Playbooks
If an alert does not have a clear owner or response path, it should not exist. Alerts without action create friction without value.
No Alert Review or Retirement Process
Many SOCs continuously add alerts but never remove them. Over time, outdated or low-value alerts clog queues and consume analyst attention.
Treating All Assets as Equal Risk
Monitoring systems without accounting for business impact guarantees noise. Critical assets deserve deeper scrutiny. Low-risk systems do not. This same prioritization logic underpins vulnerability assessment programs.
SOC Monitoring Tools: Why Tools Aren’t the Problem
SOC teams often attempt to solve monitoring challenges by adding new tools SIEM replacements, additional sensors, or new automation platforms.
Tools matter, but they are not the root issue.
Without a clear monitoring strategy:
- SIEMs become alert factories
- EDR tools generate endless notifications
- Automation amplifies noise instead of reducing it
This is where AI and automation must be applied deliberately, not bolted on. A deeper breakdown of how automation fits into SOC workflows is covered SOC AI Automation.
Are your SOC alerts creating noise or reducing risk?
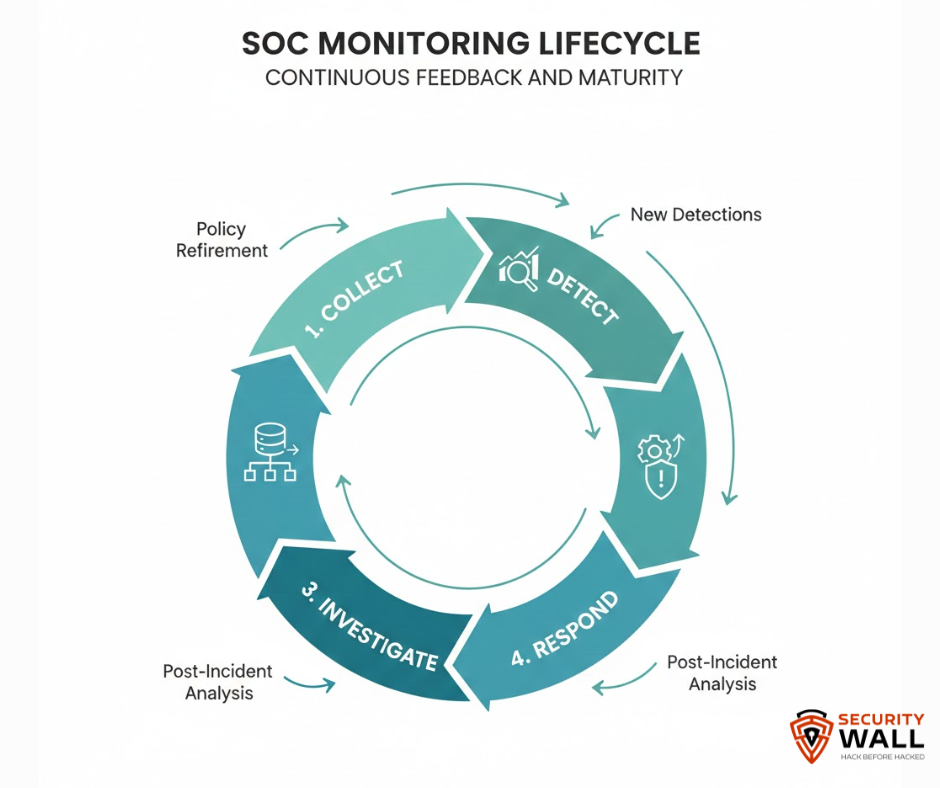
SOC Monitoring and Management as a Continuous Lifecycle
Mature SOCs treat monitoring as a continuous loop rather than a static configuration.
That lifecycle includes:
- Data collection and normalization – focused on relevance, not volume
- Detection engineering and tuning – continuously improving signal quality
- Investigation and response workflows – aligned to analyst capabilities
- Feedback and improvement – retiring ineffective alerts and refining successful ones
This approach is typically delivered through managed SOC services, where monitoring and management are treated as a single operational function.
SOC monitoring is not about seeing everything. It is about seeing what matters first.
Organizations that succeed with SOC monitoring and management are not the ones with the most data. They are the ones that prioritize risk, context, and attacker behavior and continuously refine their approach.
Monitor less. Detect better. Manage deliberately.
Need help improving SOC signal quality?
Tags
About Hamza Razzaq
Hamza Razzaq is a cybersecurity professional with 10 years of SOC operations experience, specializing in threat monitoring, incident response, and SIEM-based detection across enterprise environments.