How SOC AI Automation Reduces Alert Fatigue
Hamza Razzaq
January 27, 2026
Security Operations Centers were never designed to operate under continuous signal saturation. Yet for many organizations, the modern SOC experience is defined by endless alerts flowing directly from detection systems into ticketing tools, chat platforms, and case management systems with little to no processing in between. We've shared Modern SOC Guide earlier.
At first glance, this model appears efficient. Alerts are delivered instantly. Nothing is dropped. Everything is logged. Visibility feels complete.
In reality, this architecture creates one of the most dangerous blind spots in modern security operations.
Alert routing without intelligence is not automation. It is amplification.
Signals move faster, but understanding does not.
This article examines why webhook driven SOC workflows fail at scale, how intelligent alert pipelines change operational outcomes, and why introducing AI into SOC workflows must be approached as a security design problem, not just an efficiency upgrade.
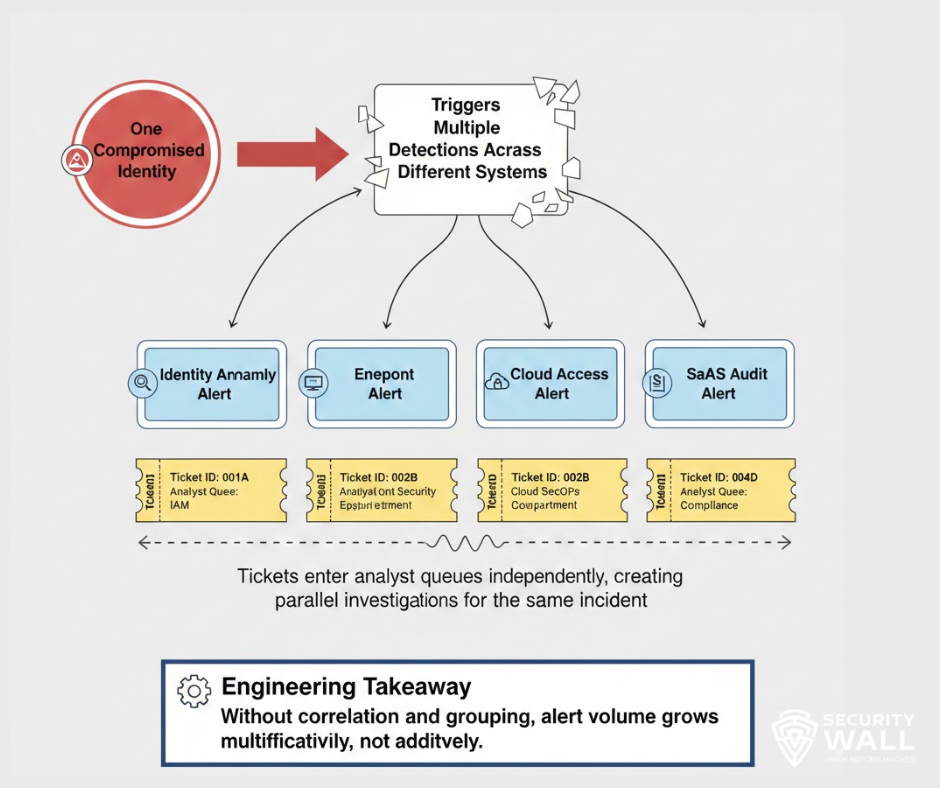
The Hidden SOC Anti Pattern: Treating Alerts as the Final Product
Most SOC architectures still follow a simple operational flow. A detection fires in a SIEM or security platform. That alert is sent directly via webhook to a ticketing system or chat channel. An analyst receives it and begins triage.
This model assumes three things that are no longer true.
It assumes alerts are inherently meaningful.
It assumes analysts already have enough context to act quickly.
It assumes alert volume will remain manageable.
Modern environments violate all three assumptions simultaneously.
Cloud infrastructure, identity systems, SaaS platforms, APIs, and automation frameworks generate signals faster than humans can reason about them. Alerts arrive stripped of business context, asset ownership, historical behavior, and threat intelligence. The SOC becomes reactive rather than investigative.
What looks like speed is actually noise moving faster.
Why Webhook Only SOC Architectures Fail at Scale
Direct alert delivery creates compounding operational and security failures as environments grow.
Duplicate detections across tools generate parallel tickets for the same underlying behavior. Analysts spend time correlating instead of responding.
Alert storms overwhelm queues. During misconfigurations or active attacks, rate limits are exceeded and high value signals are buried under low value noise.
Context switching becomes constant. Analysts manually query CMDBs, identity systems, asset inventories, and telemetry platforms just to understand what an alert refers to.
Most dangerously, alerts are treated as incidents by default. The SOC responds to symptoms instead of understanding behavior.
This is not a tooling problem. It is a pipeline problem.
Is Alert Fatigue Slowing Down Your SOC?
Get a Free Alert Fatigue & Automation Assessment
The Missing Layer: Alert Intelligence Pipelines
High performing SOCs do not treat alerts as finished artifacts. They treat them as raw inputs.
Between alert generation and human handling sits an intelligence pipeline. This pipeline transforms noisy signals into actionable security context.
Instead of sending alerts directly to tickets or chat, alerts pass through a processing layer that enriches, correlates, summarizes, and prioritizes them before a human ever sees them.
This is where modern SOC automation platforms and workflow engines become critical. Not as routers, but as decision systems. SOC automation is most effective when built on a strong monitoring and management strategy rather than deployed as a standalone solution.
What an Intelligent SOC Pipeline Actually Does
An effective alert pipeline performs transformations that manual triage cannot scale to achieve.
Alerts rarely answer the most important operational questions. Who owns the asset. Is it production or development. Is the user privileged. Has this behavior occurred before. What is the business impact.
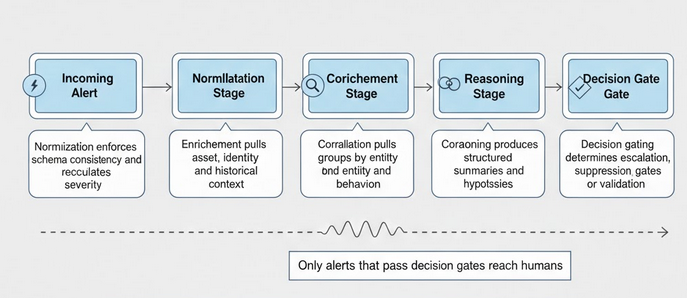
An intelligence pipeline automatically enriches alerts with CMDB data, identity and HR context, asset criticality, historical telemetry, and internal knowledge sources. Analysts begin investigations with structured context instead of fragmented signals.
Raw alerts are written for machines, not humans. AI assisted reasoning layers translate detections into structured summaries that explain what happened, why it matters, and what is already known. This does not replace analysts. It accelerates understanding and reduces time to triage.
Threat intelligence correlation transforms unknown indicators into informed decisions. Reputation checks, external intelligence sources, and internal threat data reduce uncertainty before escalation.
Automated historical queries reveal scope and impact early. Instead of manually running follow up SIEM searches, the pipeline expands investigations programmatically.
Alert grouping and deduplication reduce operational noise. The SOC reasons in terms of incidents rather than isolated events. Queueing and rate control prevent alert floods from becoming operational outages.
Human interaction becomes proactive instead of reactive. Pipelines validate with users or system owners before escalation, eliminating large classes of false positives before tickets are ever created.
AI in the SOC Changes the Threat Model
As SOCs introduce AI agents into alert pipelines, the security model fundamentally changes.
These systems are no longer passive automation. They interpret input. They summarize reality. They influence response decisions.
Alert content itself becomes an input into AI reasoning systems. If not properly controlled, malformed or malicious data can manipulate summaries, conclusions, and downstream actions. Over trusting AI generated conclusions without validation creates false confidence.
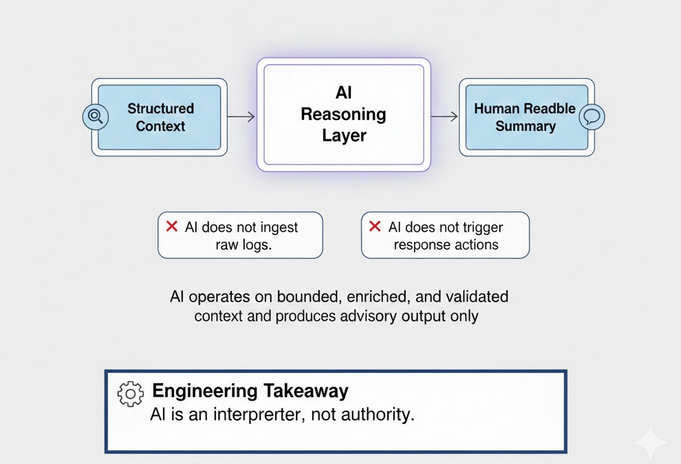
The lesson from AI security research is consistent. Any system that interprets untrusted input and produces privileged output becomes an attack surface.
SOC pipelines are no exception.
Suggested SOC Alert Intelligence Pipeline
The diagram below shows a suggested alert intelligence pipeline inspired by real world SOC workflows. Rather than routing alerts directly to ticketing systems, this design introduces a processing layer that transforms raw detections into contextualized, decision ready signals.
Suggested SOC Alert Intelligence Pipeline
SIEM · EDR · Cloud · Identity · SaaS
Canonical schema · Severity recalculation
CMDB · Asset ownership · Identity context
IOC reputation · External intelligence
Prior behavior · Scope expansion
Summarization · Contextual interpretation · Analyst assist
Grouping · Deduplication · Escalation criteria
Investigation · Decision making
Tickets only when action is required
Treat Alert Pipelines as Critical Security Infrastructure
An intelligent SOC pipeline must be designed with the same rigor as any security control.
Inputs should be validated and sanitized before reaching AI components.
AI agents should operate with constrained permissions and clearly defined scopes.
Enrichment, summarization, and execution should be separated to prevent unintended actions.
Every automated decision should be logged and auditable.
High-impact actions must keep humans in the loop.
Security teams must resist the temptation to blindly trust automation simply because it is intelligent.
From Alert Routers to Intelligence Systems
The future SOC is not faster because alerts move quicker. It is faster because analysts receive fewer, richer, and more accurate signals.
Organizations struggling with alert fatigue are not lacking tools. They are lacking transformation layers. These automation capabilities extend the core functions of a Security Operations Center, including monitoring, investigation, and response.
If alerts go straight to tickets, the SOC is operating blind.
If alerts pass through intelligence pipelines, the SOC operates with context.
The difference is not efficiency.
The difference is security.
Get a Free SOC Architecture Review
Validate Your SOC Design, Tooling & Detection Coverage
Tags
About Hamza Razzaq
Hamza Razzaq is a cybersecurity professional with 10 years of SOC operations experience, specializing in threat monitoring, incident response, and SIEM-based detection across enterprise environments.