NESA Audit & Assessment Process
Hisham Mir
January 8, 2026

Most organizations do not fail NESA assessments because of missing security tools. They fail because governance, evidence, and accountability are not structured in a way regulators expect.
A NESA audit is not a certification exercise or a third-party review. It is a regulatory assessment focused on how effectively an organization manages cyber risk, protects critical systems, and demonstrates compliance with national requirements. Understanding how this process works—before assessment timelines begin is essential to avoiding unnecessary findings and regulatory exposure.
NESA audits are conducted to evaluate an organization’s alignment with the UAE’s national cybersecurity framework, which is explained in detail in our guide to NESA in the UAE
What Is a NESA Audit or Assessment?
A NESA audit is not a certification and not a voluntary third-party review. It is a formal regulatory assessment conducted under the UAE Information Assurance (IA) framework, overseen by national cybersecurity authorities.
The purpose of a NESA assessment is to evaluate whether an organization:
- Meets mandatory cybersecurity and information assurance requirements
- Has governance, risk management, and controls aligned with national expectations
- Can demonstrate evidence-based compliance, not just intent
Unlike ISO or industry audits, NESA assessments focus on national impact, maturity, and resilience especially for entities supporting critical or regulated services.
How NESA Evaluates Compliance
NESA evaluates compliance through a structured, evidence-driven model, rather than a simple pass/fail checklist.
Assessments typically focus on:
- Governance and accountability
- Risk assessment and treatment
- Integrated security controls (logical, physical, personnel)
- Incident management and escalation readiness
- Business continuity and resilience
Each area is assessed based on how well controls are defined, implemented, operated, and evidenced. A detailed understanding of NESA compliance requirements is essential before entering this phase.
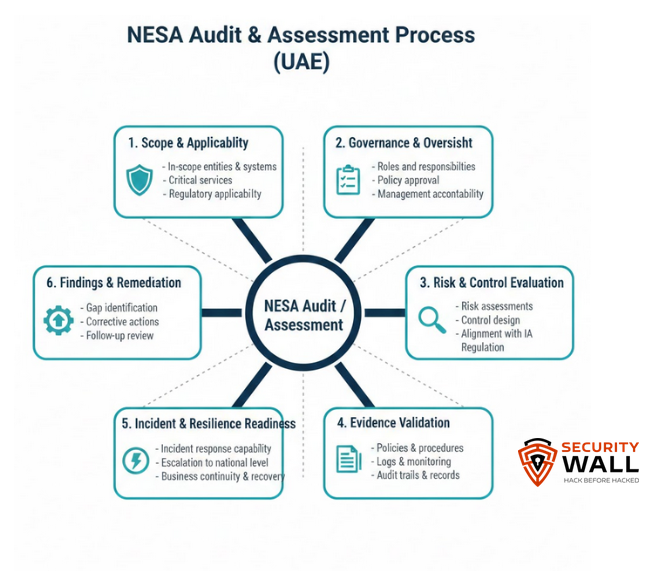
Typical Phases of a NESA Assessment
While the exact structure may vary depending on sector and criticality, most organizations experience the assessment process in distinct phases.
1. Scope Definition and Applicability Confirmation
Before any evaluation begins, NESA confirms:
- Which entities, systems, and services are in scope
- Whether the organization supports critical or regulated functions
- Applicable domains under the IA Regulation
Poor scoping is one of the most common causes of extended assessments and regulatory friction.
2. Control and Governance Review
At this stage, NESA evaluates whether required controls exist on paper and in practice. This includes governance structures, policies, risk processes, and oversight mechanisms.
Organizations that rely on informal practices or undocumented ownership often encounter findings early in this phase.
3. Evidence Validation
This is where most organizations struggle.
NESA does not accept verbal explanations or assumed controls. Evidence must be:
- Documented
- Approved
- Current
- Traceable to specific controls
Logs, reports, records, and review artifacts are examined to confirm controls are actively operating.
4. Findings, Gaps, and Remediation
Where gaps are identified, organizations may be required to:
- Address deficiencies within defined timelines
- Provide updated evidence
- Demonstrate corrective actions
In higher-risk scenarios, follow-up assessments or escalated oversight may occur.
Who Can Conduct a NESA Audit?
This is a critical and often misunderstood point.
Only the national cybersecurity authority (via NESA/SIA) can conduct or mandate an official NESA regulatory audit or assessment.
Organizations cannot self-certify, and third-party firms cannot issue NESA compliance certification.
Talk to a NESA expert about your compliance and risk challenges
What Third Parties Can Do
While external consultants cannot perform the official audit, they can:
- Conduct readiness assessments
- Identify gaps against NESA requirements
- Help normalize evidence and documentation
- Prepare organizations for regulatory review
This distinction is essential. Engaging support before regulatory assessment significantly reduces findings and operational disruption.
Common Reasons Organizations Fail NESA Assessments
Across sectors, the same issues appear repeatedly not due to lack of security tools, but lack of structure.
Common failure points include:
- Controls implemented without documented approval
- Evidence scattered across teams or systems
- Risk assessments that are outdated or incomplete
- Incident response plans that were never tested
- Unclear ownership between IT, risk, and leadership
These issues are preventable with proper preparation.
How to Prepare Before a NESA Audit
Effective preparation focuses on readiness, not reaction.
Organizations should:
- Validate scope and applicability early
- Conduct internal or external readiness reviews
- Align controls to documented risk decisions
- Centralize and validate evidence
- Perform internal reviews before regulator engagement
This approach allows organizations to enter assessments with confidence rather than urgency.
Many organizations choose to formalize this process through structured NESA compliance services that focus specifically on readiness, evidence quality, and regulatory alignment.
When to Engage External Support
Timing matters.
Organizations typically engage external expertise when:
- Assessment timelines are approaching
- Internal teams lack NESA-specific experience
- Evidence requirements are unclear
- Multiple frameworks must be aligned
- Regulatory exposure is high
Engaging support early reduces remediation cost, operational disruption, and regulatory risk. For organizations managing multiple obligations, this should align with broader cybersecurity and compliance services across governance and risk.
NESA Audits Are Predictable
NESA assessments follow a structured, well-defined regulatory model. Organizations that fail are rarely surprised by what was required—only by how rigorously it was evaluated.
Audit readiness is not about passing a test. It is about demonstrating control, accountability, and resilience in line with national expectations.
Organizations that treat readiness as a continuous discipline not a last-minute exercise—are consistently better positioned to meet NESA regulatory scrutiny.
Related Reading
- Before preparing for an audit, understand the regulatory scope and applicability by reading our overview of NESA in the UAE.
- Review the controls, domains, and documentation evaluated during audits in our guide to NESA compliance requirements.
- Validate readiness and identify gaps ahead of assessments using our NESA compliance checklist.
- For end-to-end audit preparation, remediation, and compliance support, explore our NESA compliance services.
- Understand how NESA assessments fit within broader regulatory obligations via our compliance solutions.
Frequently Asked Questions (FAQs)
Who conducts official NESA audits?
Official NESA audits and assessments are conducted or mandated by the national cybersecurity authority (via NESA/SIA). Third parties cannot issue NESA certification.
Can a consulting firm perform a NESA audit?
No. Consulting firms can conduct readiness or gap assessments, but only NESA can perform regulatory audits.
Is NESA audit the same as ISO certification?
No. NESA is a regulatory assessment, not a voluntary certification like ISO 27001.
What happens if gaps are found during a NESA assessment?
Organizations may be required to remediate gaps, provide additional evidence, or undergo follow-up evaluation depending on severity.
When should organizations start preparing for a NESA audit?
Preparation should begin months in advance, especially for entities supporting critical or regulated services.
Tags
About Hisham Mir
Hisham Mir is a cybersecurity professional with 10+ years of hands-on experience and Co-Founder & CTO of SecurityWall. He leads real-world penetration testing and vulnerability research, and is an experienced bug bounty hunter.
