JWT Security: Best Practices to Protect Web Tokens
Hisham Mir
January 2, 2026

JSON Web Tokens (JWTs) sit at the center of modern authentication and API security. They are simple to issue, easy to transport, and dangerously easy to misuse.
Most JWT-related incidents are not caused by broken cryptography. They are caused by incorrect assumptions about what JWTs guarantee, incomplete validation, and a lack of visibility into how tokens behave once they are issued.
We are writing this article because, in real production systems, JWT failures are rarely obvious. Tokens often verify, applications continue to function, and vulnerabilities remain hidden until abuse occurs and to approach JWT security the way experienced application security teams do by identifying real failure patterns, applying enforceable controls, and verifying tokens using security focused analysis rather than trust or guesswork.
For Security & Engineering Leads
- JWTs provide integrity and authenticity not confidentiality or authorization
- Most JWT vulnerabilities stem from validation gaps, not token format
- Secure JWT usage requires strict claim enforcement, algorithm controls, and short lifetimes
- Decoding tokens is insufficient; security analysis requires verification and context
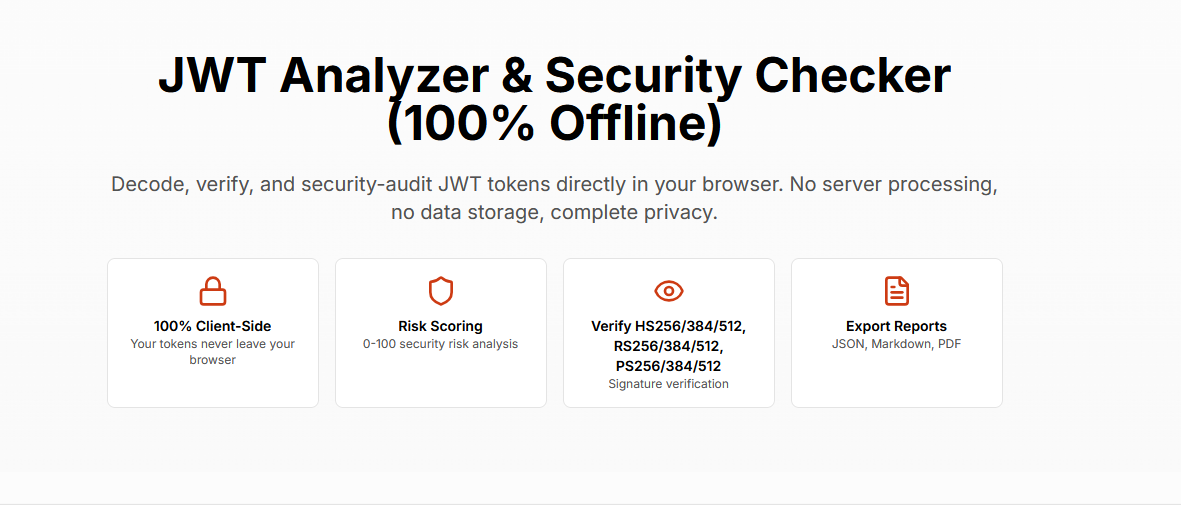
- The SecurityWall JWT Analyzer exists to validate JWTs the way attackers abuse them — safely, locally, and repeatably
1. Why JWT Security Continues to Fail in Production
JWTs are attractive because they are stateless and portable. That same portability is what makes failures so costly.
In real use case incidents, JWTs fail because:
- Validation logic is incomplete or inconsistent across services
- Developers trust decoded payloads without verifying signatures
- Tokens are treated as authorization objects instead of identity assertions
- Expiration and audience checks are treated as optional
- Tokens are never independently reviewed once “it works”
The result is predictable: token forgery, replay, privilege escalation, and long-lived access after compromise.
2. The JWT Security Contract (What JWTs Actually Guarantee)
A JWT makes exactly three security guarantees and no more.
- Integrity – the token has not been modified (if the signature is verified)
- Authenticity – the token was issued by a trusted signer
- Claim transport – claims are delivered in a compact, signed structure
What JWTs Do Not Guarantee
- Confidentiality (payloads are readable)
- Authorization enforcement
- Token freshness
- Replay protection
- Client-side trust
Every JWT security issue maps back to a violation of this contract usually by assuming JWTs do more than they do.
3. Real JWT Failure Patterns
Instead of abstract “threat models”, these are patterns that repeatedly appear in production systems.
3.1 Signature & Algorithm Failures
What goes wrong
- Accepting
alg: none - Allowing algorithm switching
- Verifying RS256 tokens with HMAC logic
- Falling back to unsafe algorithms
Impact
Full authentication bypass.
3.2 Weak or Reused Signing Secrets (HMAC)
What goes wrong
- Short or guessable secrets
- Secrets committed to repositories
- Same secret used across environments
Impact
Anyone can forge valid tokens.
3.3 Claim Validation Failures
What goes wrong
- Missing
exp,iss, oraud - Excessively long token lifetimes
- Ignoring
nbforiat
Impact
Replay attacks, cross-service token reuse, lateral movement.
3.4 Trust Boundary Violations
What goes wrong
- Client-side JWT validation
- Trusting decoded payloads without verification
- “Internal service” exceptions
Impact
Trivial impersonation.
3.5 Sensitive Data Exposure
What goes wrong
- PII in payloads
- Roles or permissions embedded in tokens
- Session metadata exposed to clients
Impact
Privacy violations and privilege abuse when tokens leak.
4. Why JWT Security Requires Analysis, Not Just Decoding
Most developers interact with JWTs by decoding them.Security teams must verify and interpret them.
Proper JWT analysis requires:
- Cryptographic signature verification
- Algorithm safety checks
- Claim completeness and correctness
- Token lifetime and replay window analysis
- Detection of weak secrets
- Risk aggregation
This is where general-purpose decoders fall short and where dedicated tools matter.
5. What JWT Tools Exist and Their Limitations
JWT Decoders
- Show header and payload
- No verification
- No security insight
Partial Verifiers
- Check signatures
- No claim enforcement
- No risk context
Enterprise Scanners
- Broad coverage
- Limited token-level investigation
- Not designed for daily engineering workflows
6.SecurityWall JWT Analyzer Vs Typical JWT Tools
Most JWT tools focus on visibility decoding headers and payloads so developers can see what a token contains. While useful, this stops short of answering the question security teams actually need to answer:
“Is this token safe to trust?”
The JWT Analyzer from SecurityWall is designed specifically to close that gap.
Rather than acting as a simple decoder, it performs security-oriented JWT inspection, helping teams validate tokens against real-world failure patterns.
SecurityWall’s JWT Analyzer vs Other Tools Comparison
| Capability | Typical JWT Tools | SecurityWall JWT Analyzer |
|---|---|---|
| Decode JWT | ✅ | ✅ |
| Verify Signature | ⚠️ Partial | ✅ Full cryptographic |
| Algorithm Abuse Detection | ❌ | ✅ |
| Weak Secret Detection | ❌ | ✅ |
| Claim Enforcement | ❌ | ✅ |
| Lifetime Risk Analysis | ❌ | ✅ |
| Payload Sensitivity Flags | ❌ | ✅ |
| Security Risk Scoring | ❌ | ✅ |
| Client-Side Only | ❌ | ✅ |
| Exportable Reports | ❌ | ✅ |
What It Focuses On
- Client-Side Token Analysis
All JWT processing happens locally in the browser, allowing real production tokens to be analyzed without sending data to external servers. - JWT Decode View
Separates the header, payload, and signature while clearly distinguishing standard claims from custom application claims. - Explicit Signature Verification
Detects the signing algorithm used and requires the correct secret or public key to verify the token cryptographically. - Verification Status Indicator
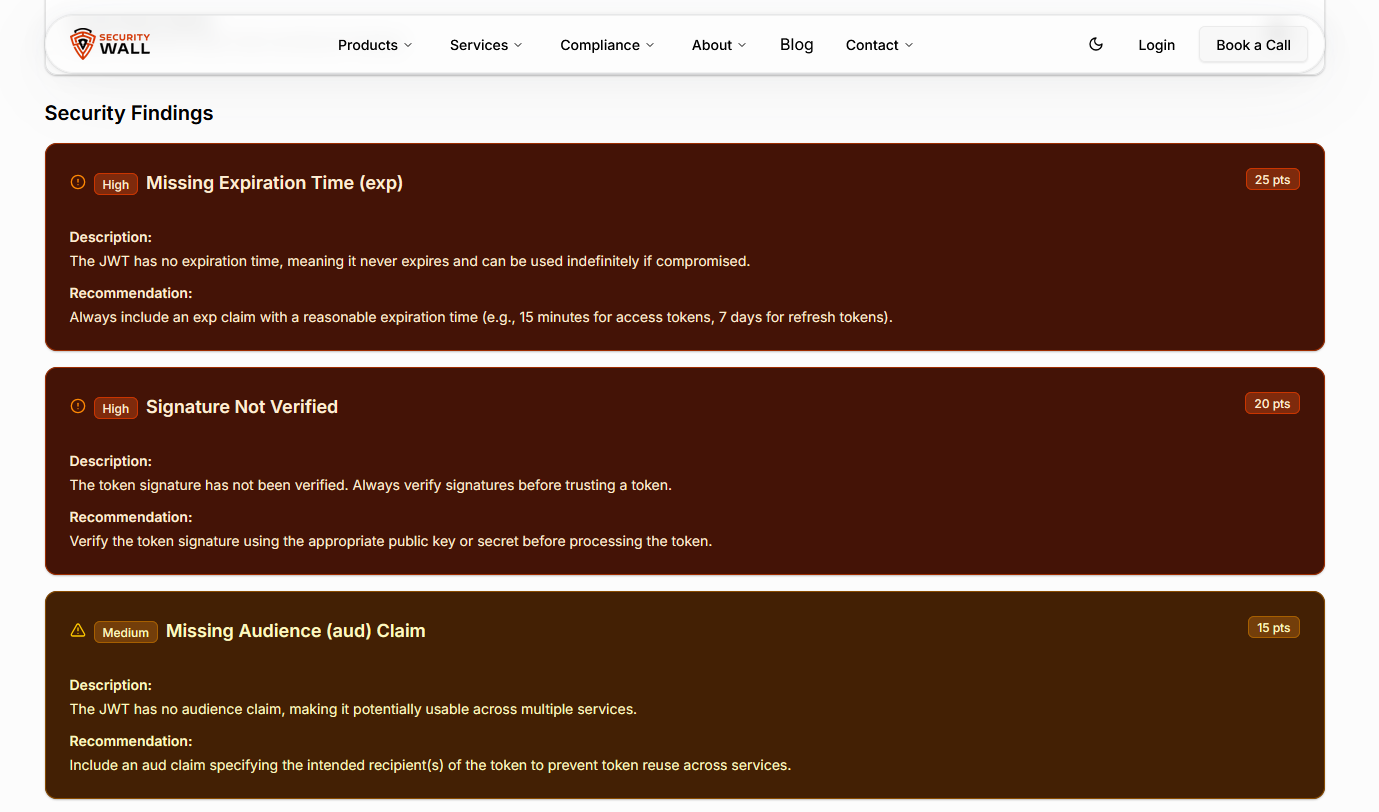
Clearly shows whether a token has been successfully verified, partially verified, or not verified at all. - Security Findings Engine
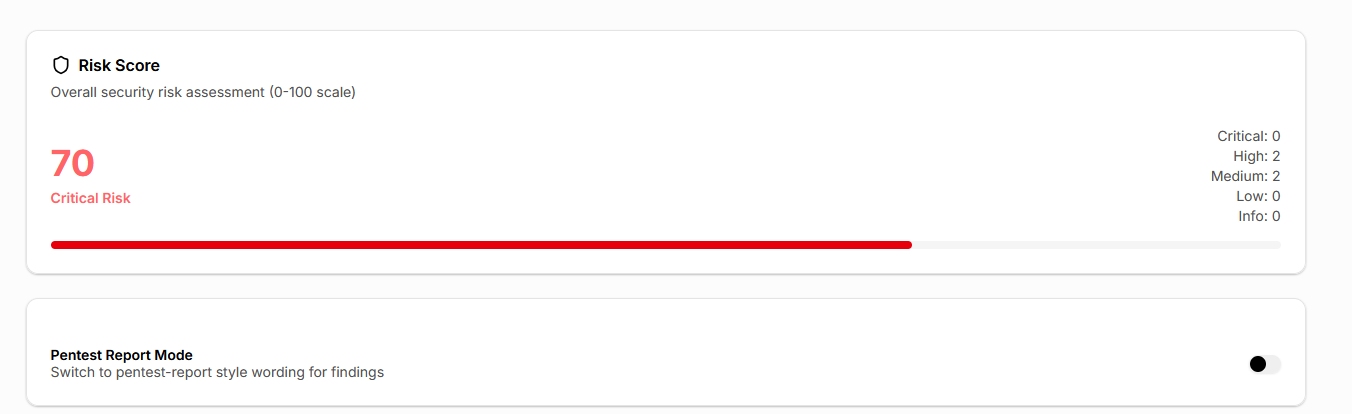
Automatically identifies common JWT security issues such as missing expiration, issuer, audience, and unverified signatures. - Risk Scoring (0–100)
Aggregates all findings into a single security risk score to quickly assess whether a token is safe to trust. - Token Timeline Visualization
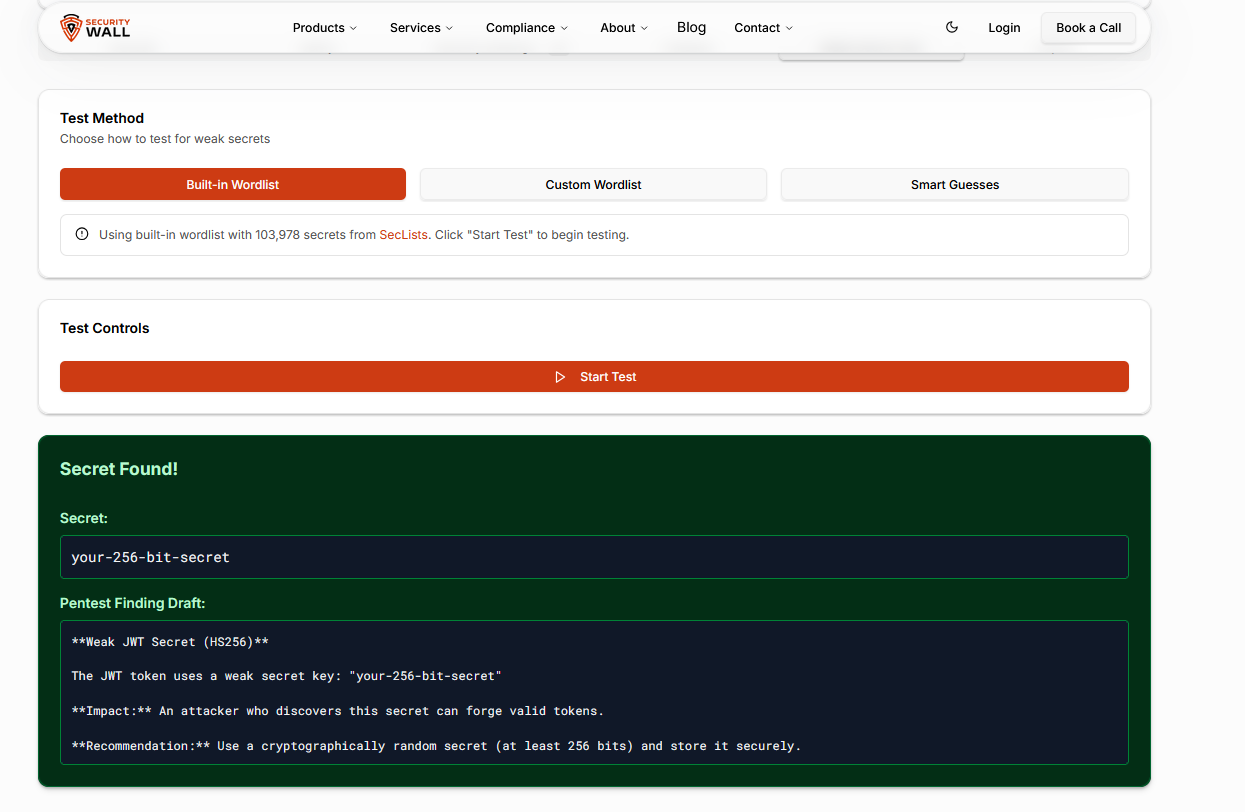
Displays issued-at, not-before, and expiration times visually to highlight lifetime exposure and replay risk. - Weak Secret Detection (HMAC)
Tests HMAC-signed tokens against built-in and custom wordlists to identify guessable or reused signing secrets. - Pentest Finding Generation
Converts detected issues into security assessment–style findings with impact and remediation guidance. - Payload Sensitivity Detection
Flags potentially sensitive data embedded in the JWT payload that may increase impact if the token leaks. - Report Export (JSON, Markdown, Print)
Allows findings to be exported in multiple formats for reviews, audits, and security documentation. - Sensitive Data Redaction
Redacts payload values during export to prevent accidental leakage of authentication data. - Pentest Report Mode
Formats findings specifically for penetration testing and application security reporting workflows.
Designed for Real Tokens, Not Samples
A key differentiator is that all analysis is performed entirely in the browser, without sending tokens or secrets to a server. This makes the tool suitable for inspecting real production tokens during security reviews, incident response, and pre-release validation not just example data.
From Inspection to Security Judgment
Instead of presenting raw token data, the JWT Analyzer provides security context helping teams understand why a token may be dangerous, not just what it contains.
This makes it useful not only for developers debugging authentication issues, but also for security engineers performing reviews, assessments, and audits.
8. Where the JWT Analyzer Fits in Real Workflows
- During authentication implementation
- As part of AppSec reviews
- During penetration testing
- Incident response investigations
- Pre-production security gates
JWT issues are inexpensive to fix early and costly to fix after compromise.
A dedicated JWT Security Analyzer provides the visibility and judgment needed to validate tokens the same way attackers abuse them safely and repeatably.
Tags
About Hisham Mir
Hisham Mir is a cybersecurity professional with 10+ years of hands-on experience and Co-Founder & CTO of SecurityWall. He leads real-world penetration testing and vulnerability research, and is an experienced bug bounty hunter.