JWT Pentesting: A Practical Guide to JSON Web Token Security & Testing Techniques
Hisham Mir
January 8, 2026

Our previous guides cover how to securely design, configure, and analyze JSON Web Tokens including JWT Security Best Practices, the hands-on JWT Analyzer Security Checker Guide, and JWT Analyzer vs Other Token Debuggers this post shifts the focus entirely to JWT pentesting. Instead of defensive configuration or tool usage, it examines how JWT implementations break in real-world applications, how attackers and penetration testers identify those weaknesses, and which testing techniques expose flawed trust assumptions, authorization logic, and token validation failures during security assessments.
Understanding JWTs from an Attacker’s Perspective
A JWT is more than just a bearer token it is executable trust data. Every claim inside a JWT directly influences authorization decisions made by the backend.
From a pentester’s point of view, JWT analysis starts with three fundamental questions:
- Who issued the token?
- How is the token validated?
- What security assumptions does the backend make about its contents?
The moment an application trusts token claims without strong verification, it creates an opportunity for privilege escalation, impersonation, or account takeover.
JWT Attack Surface: Where Pentesters Should Focus
JWT vulnerabilities rarely exist in isolation. They typically emerge from design assumptions combined with implementation shortcuts.
Key areas to examine during a JWT pentest include:
- Token signature verification logic
- Algorithm handling (
algtrust) - Claim-based access control decisions
- Token lifetime enforcement
- Key management and rotation
- Backend consistency across microservices
Each of these areas introduces distinct failure modes that attackers can exploit when testing real systems.
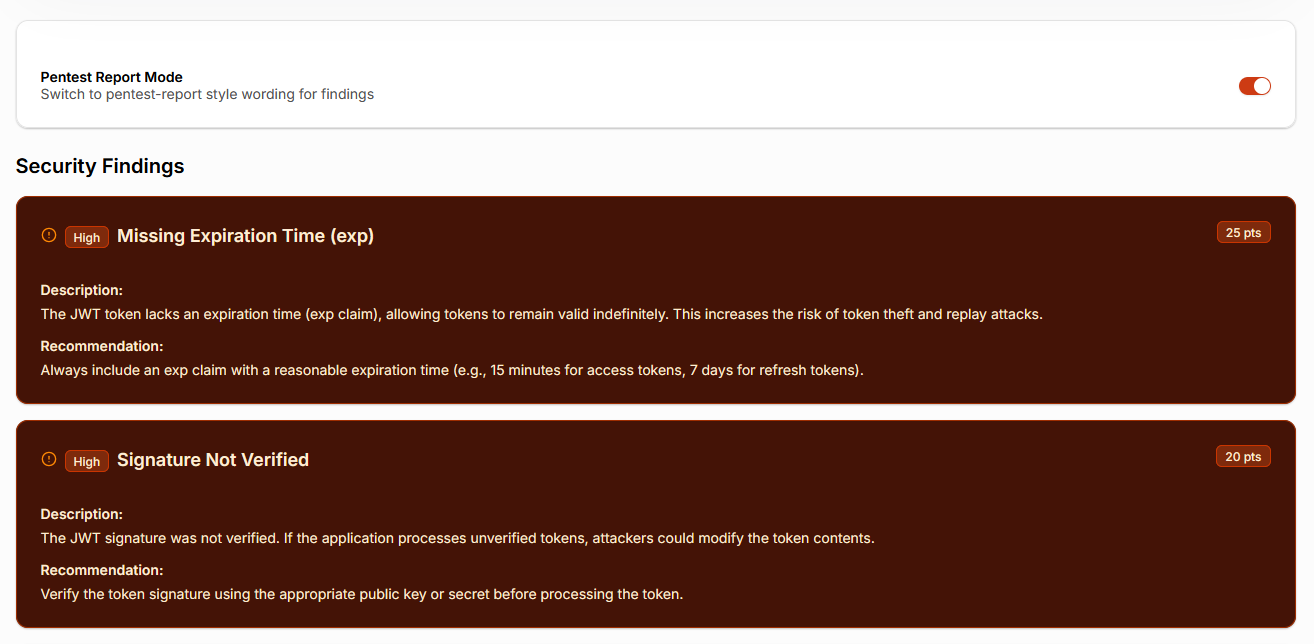
Core JWT Pentesting Techniques
1. Token Structure & Claim Manipulation
JWTs are Base64URL-encoded and easily decoded without a secret. This transparency is intentional and dangerous when developers assume claims are “safe.”
Pentesters should inspect tokens for:
- Privileged claims (
role,admin,permissions) - User identifiers (
sub,uid,email) - Application-specific logic flags
- Environment or tenant identifiers
Testing involves modifying claims and observing backend behavior — especially when authorization decisions rely solely on claim values rather than server-side validation.
2. Signature & Algorithm Testing
One of the most common JWT security failures occurs when applications incorrectly trust the token’s declared algorithm.
Pentesting scenarios often include:
- Algorithm confusion (
RS256↔HS256) - Weak or improperly stored secrets
- Disabled or partially implemented signature verification
- Inconsistent verification across services
This class of issues remains a recurring source of authentication bypasses and should always be included in JWT testing scopes.
3. Token Expiry & Session Handling Weaknesses
JWTs are stateless by design but that does not mean they should be immortal.
Pentesters should test:
- Acceptance of expired tokens
- Ignored
nbf(Not Before) claims - Long-lived access tokens without rotation
- Absence of revocation mechanisms
Applications that treat JWTs like permanent session cookies expose themselves to replay attacks and account persistence long after compromise.
4. Trust Boundary Violations in Microservices
In modern architectures, JWTs often travel across multiple internal services. A frequent design flaw is assuming internal trust without revalidation.
JWT pentesting should include:
- Passing modified tokens between services
- Observing inconsistent authorization decisions
- Identifying services that skip verification entirely
- Detecting internal endpoints that trust upstream authentication blindly
These flaws often enable attackers to pivot laterally within distributed systems.
Automating JWT Analysis During Pentests
Manual JWT testing is error-prone and time-consuming — especially when dealing with complex tokens, nested claims, or multiple environments.
Using a dedicated JWT inspection tool allows pentesters to:
- Decode, edit, and re-sign tokens safely
- Test algorithm behavior consistently
- Detect structural and logical weaknesses faster
- Validate token handling across different backends
For hands-on testing and deep token inspection, the SecurityWall JWT Analyzer provides a purpose-built environment for analyzing JWT behavior during security assessments.
Use the JWT Analyzer to inspect, modify, and validate tokens during penetration testing. If you want a deeper walkthrough of its capabilities, see the JWT Analyzer Security Checker Guide.
JWT Pentesting Attack Matrix
| Attack Category | What to Test | Common Weakness | Security Impact |
|---|---|---|---|
| Claim Manipulation | Modify role, scope, permissions |
Backend trusts client-controlled claims | Privilege escalation |
| Algorithm Confusion | Switch alg (RS256 ↔ HS256) |
Algorithm value trusted from token | Token forgery |
| Signature Bypass | Remove or tamper with signature | Missing or partial verification | Authentication bypass |
| Expired Token Abuse | Replay expired JWTs | exp or nbf not enforced |
Persistent unauthorized access |
| Token Replay | Reuse captured tokens | No rotation or revocation logic | Account takeover |
| Weak Secret Usage | Brute-force HMAC signing key | Low-entropy or reused secrets | Token signing compromise |
| Key Confusion | Use public key as HMAC secret | Incorrect key handling | Forged trusted tokens |
| Audience Abuse | Modify aud claim |
Audience not validated | Cross-service access |
| Issuer Abuse | Change iss value |
Issuer not enforced | Acceptance of attacker-issued tokens |
| Microservice Trust | Pass modified JWT internally | No revalidation between services | Lateral movement |
| Excessive Token Lifetime | Test long-lived exp |
Overly permissive expiration | Long-term compromise |
| Logout Bypass | Use token after logout | Stateless token misuse | Session persistence |
Avoiding Common JWT Testing Pitfalls
Many pentests fail to uncover JWT vulnerabilities not because they don’t exist but because testing is too shallow.
Common mistakes include:
- Only decoding tokens without modifying them
- Ignoring backend authorization logic
- Skipping internal service validation
- Treating JWTs as “secure by default”
- Overlooking token lifecycle and revocation logic
Effective JWT pentesting requires active manipulation, behavioral observation, and cross-service testing not just static inspection.
JWT Security Beyond Pentesting
While this guide focuses on identifying weaknesses, long-term security requires correct architectural decisions.
For defensive guidance, review:
- JWT Security Best Practices — a strategic overview of secure token design and validation
- JWT Analyzer vs Other Token Debuggers — understanding why generic debuggers fall short for security testing
- Guide for JWT Analyzer & Security Checker Tool — Learn more about JWT Analyzer Tool
These resources complement pentesting efforts by addressing prevention, not just detection.
JWT pentesting is no longer avoidable. As JWTs increasingly control access to sensitive APIs, internal services, and user data, even small implementation flaws can lead to catastrophic breaches. A structured testing approach combined with specialized tooling enables security teams to identify weaknesses before attackers do. By treating JWTs as best practices, not just authentication tokens, organizations can significantly reduce their attack surface and improve overall application security.
Tags
About Hisham Mir
Hisham Mir is a cybersecurity professional with 10+ years of hands-on experience and Co-Founder & CTO of SecurityWall. He leads real-world penetration testing and vulnerability research, and is an experienced bug bounty hunter.