JWT Analyzer vs Other Token Debuggers: Choosing the Right Tool for Security Validation
Hisham Mir
January 7, 2026
In earlier articles, we examined how JWT implementations fail in practice and how to use the JWT Analyzer & security checker. This post builds on that foundation, but shifts the focus away from JWT mechanics and tooling walkthroughs. Instead, it addresses a recurring decision point we see across engineering and security teams when token inspection is sufficient, and when security-grade JWT analysis is required.
While JWTs themselves are well understood, the distinction between decoding tokens and validating trust is often blurred in production environments. This article explores that gap directly, comparing JWT analyzers and token debuggers through the lens of real security workflows, risk ownership, and operational responsibility. It is written for teams that already understand JWTs and are making tooling decisions that affect production security, not just development convenience.
The Problem: Token Tools and Misaligned Expectations
As JWT adoption increased, so did the tooling around it. Developers and security engineers now have access to a range of token inspection and analysis tools. What is often overlooked is that these tools solve fundamentally different problems.
Most JWT tools fall into two categories:
- Token Debuggers – Tools that decode JWT structure to assist with development and debugging.
- JWT Analyzers – Tools that assess token trust, validation logic, claim requirements, and potential security failures.
Confusion between these categories often leads to misuse: teams assume a token is secure because it decodes cleanly. In reality, decoded tokens can still violate basic security expectations such as proper expiration, valid claims, secure signing, and resistance to replay attacks.
Before selecting a tool, teams must first clarify whether they intend to inspect a token’s contents for structure or validate a token for security correctness.
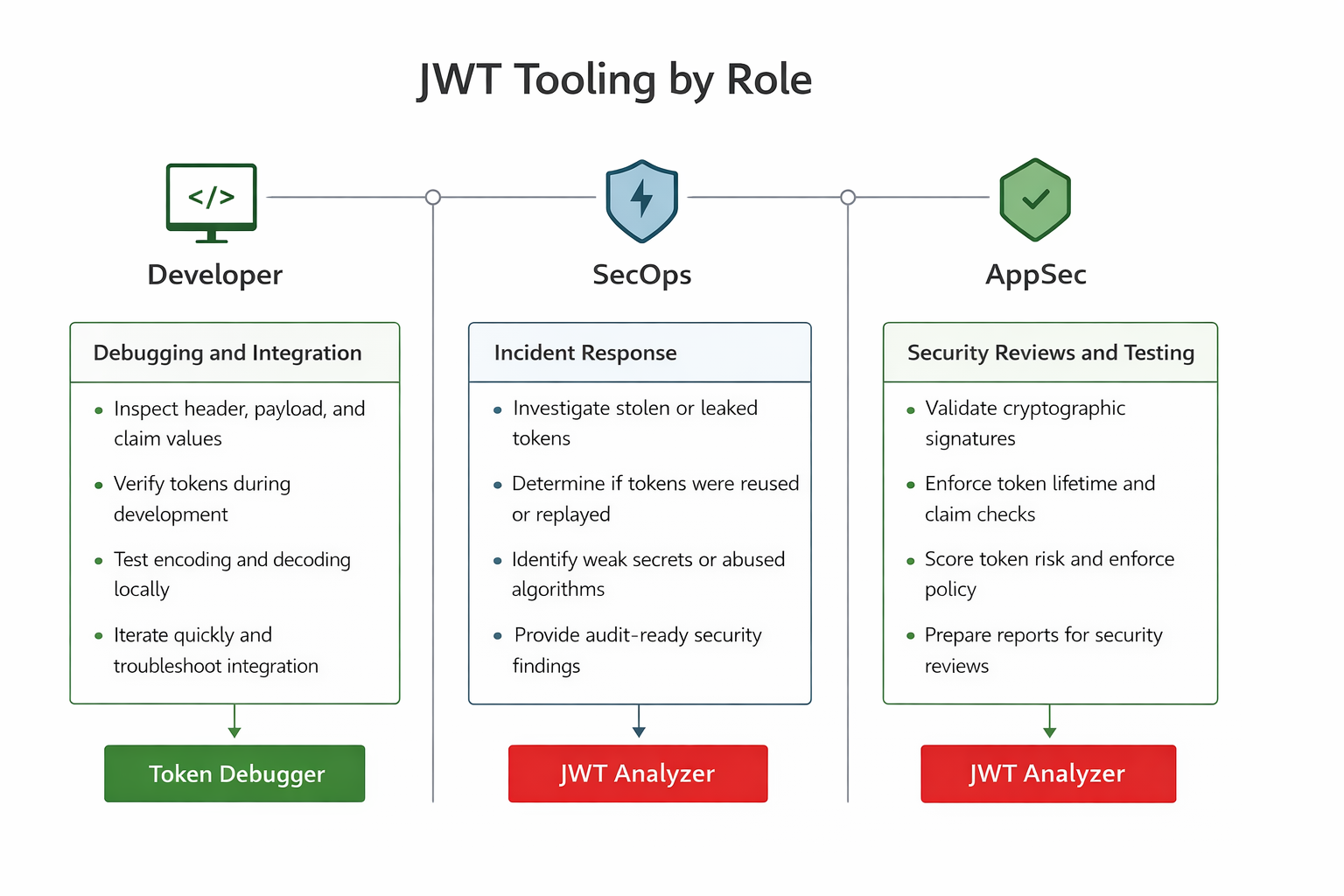
What Token Debuggers Actually Do
Token debuggers are optimized for rapid token inspection and convenience. They take an encoded JWT and display its constituent parts header, payload, and signature typically in a readable JSON format.
This is valuable for development workflows. For example:
- Verifying that a claim is being set during token issuance
- Confirming encoding formats during integration testing
- Debugging a local issue where a token appears malformed
However, token debuggers are not designed to provide security assurance. They do not validate whether:
- A token’s signature was cryptographically verified using the correct key
- Required claims (such as issuer, audience, or expiration) are enforced
- Token lifetime policies are appropriate
- The signing secret is robust against brute-force attacks
In short, debuggers provide visibility, not verification. Read in detail how JWT Analyzer & Security Checker works.
Understanding JWT Analyzer & Security Checker Capabilities
A JWT analyzer shifts focus from interpretation to evaluation. Rather than simply showing what a token contains, it answers whether a token can be trusted within defined security parameters.
A security oriented analyzer performs:
- Cryptographic signature verification
- Enforcement of required claims
- Assessment of token lifetime and replay risk
- Detection of weak signing keys (e.g., weak HMAC secrets)
- Aggregated risk scoring and structured security findings
These capabilities align with what experienced application security teams expect during threat modeling, code review, risk assessment, or incident response.
For example, a token with an expired signature or missing audience claim may decode perfectly but it should not be considered secure. A proper analyzer highlights these risks, whereas a debugger simply displays them.
The SecurityWall JWT Analyzer embodies this model: it is designed for independent verification and risk assessment across production and pre-production environments, not just token decoding.
You can explore these capabilities directly in the JWT Analyzer tool on SecurityWall.
Practical Differences: Debuggers vs Analyzers
Rather than listing features, it is useful to view the differences through the lens of real engineering decisions.
| Evaluation Dimension | Token Debuggers | SecurityWall JWT Analyzer |
|---|---|---|
| Primary Purpose | Token inspection and debugging | Security validation and trust assessment |
| Signature Verification | Optional or superficial | Mandatory cryptographic verification |
| Claim Validation | Manual inspection only | Automated enforcement and findings |
| Token Lifetime Analysis | Raw timestamps only | Timeline visualization and risk assessment |
| Weak Secret Detection (HMAC) | Not supported | Built-in and configurable testing |
| Security Context | Left to user interpretation | Structured findings with severity |
| Risk Scoring | Not available | Aggregated 0–100 risk score |
| Production Token Safety | Often unsafe or discouraged | Client-side analysis only |
| Audit & Review Readiness | Manual interpretation required | Exportable, review-ready reports |
| Best Use Case | Development and debugging | Security reviews, pentesting, incident response |
During Development
- Token Debugger: Useful for quick visibility into token format and claim structure.
- JWT Analyzer: Not typically required unless security validation is part of the development workflow.
During Security Reviews
- Token Debugger: Limited value — decoding does not indicate security posture.
- JWT Analyzer: Essential — highlights missing claims, verification failures, and risk points.
During Incident Response
- Token Debugger: Does not indicate whether a token should have been trusted.
- JWT Analyzer: Critical — provides evidence of whether a token was improperly issued or accepted.
Pre-Production Validation
- Token Debugger: Helps with syntax checks.
- JWT Analyzer: Helps with security assurance and validation of deployment readiness.
In these contexts, it becomes clear that token debuggers and JWT analyzers serve distinct purposes. Using a debugger as a surrogate for security validation creates gaps that attackers can exploit.
Why JWT Verification and Security Context Matter
Token inspection is inherently shallow: it reveals what is, not what should be. Security failures often occur not because tokens are malformed but because they are misused, accepted in inappropriate contexts, or issued with unsafe characteristics.

Examples of real-world failure patterns include:
- Tokens that never expire or have excessive lifetimes
- Tokens accepted by services without signature verification
- Missing issuer or audience claims leading to token reuse
- Weak signing secrets leading to forgery
These are not developer mistakes they are architectural failures that surface when assumptions about JWT safety go unverified.
A tool that only decodes tokens does not uncover these conditions. A tool built for security analysis does.
Case for Using a Dedicated JWT Analyzer
In security-critical environments, the following questions must be answered consistently:
- Was this token cryptographically verified using the correct key?
- Are all required claims present and valid?
- Is the token lifetime appropriate given context and threat model?
- Does the token expose data or permissions that raise risk?
- Does the token conform to organizational security policy?
A JWT analyzer provides answers that support these decisions. The SecurityWall JWT Analyzer combines real-world security checks with local processing (so tokens and secrets remain private), structured risk scoring, and exportable findings.
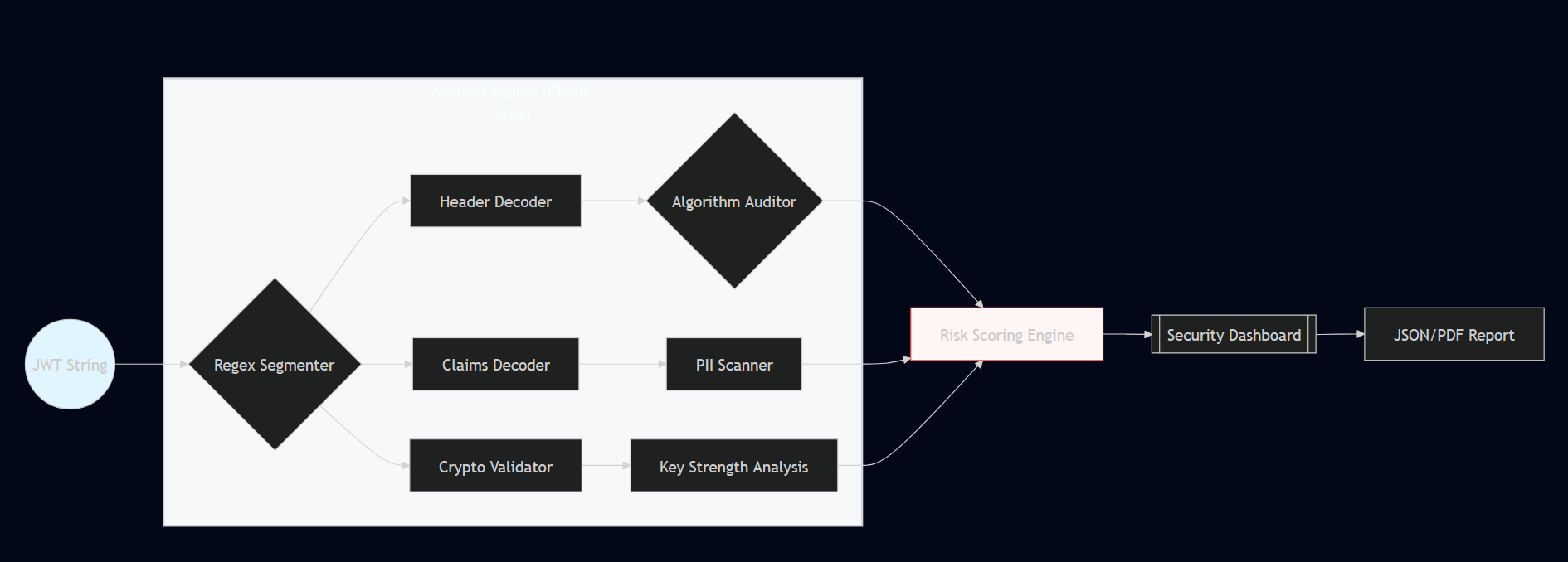
This approach is suitable for security reviews, architecture validation, penetration testing, and incident response.
When Token Debuggers Still Make Sense
There are valid use cases for token debuggers:
- Early development and rapid iteration
- Simple format or encoding validation
- Learning how JWTs are structured
Their limitations only become problematic when they are used as substitutes for verification and risk assessment.
A mature security process uses both: debuggers where convenience is needed, and analyzers where verification and security judgment matter.
JWT Analyzers and OAuth Tooling
Search queries often conflate JWT analyzers with OAuth tools, but these address different layers of security.
OAuth tooling is concerned with authorization flows, token exchange, and scope enforcement. JWT analyzers are concerned with the security properties of JWT artifacts themselves.
In environments where OAuth tokens are implemented as JWTs, both types of tools have a role. However, a JWT analyzer does not replace OAuth tooling, and OAuth tooling does not replace JWT analysis.
Making the Right Tool Choice
Choosing between token debuggers and JWT analyzers should be based on the type of decision you are making:
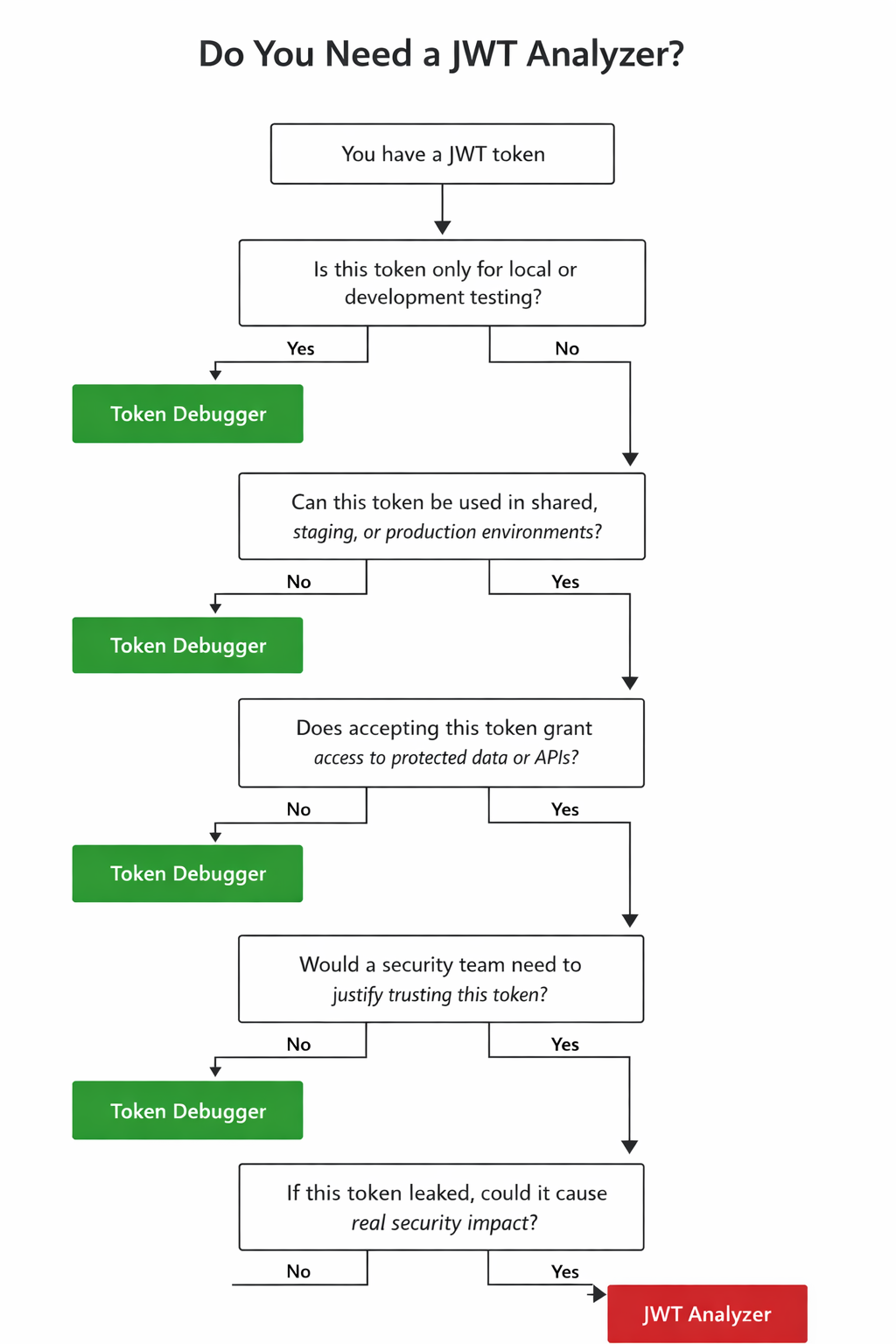
- For quick developmental inspection: token debuggers
- For security assurance and validation: JWT analyzers
Using the right tool for the right task avoids false confidence and reduces the risk of silent token vulnerabilities.
You can evaluate tokens with security context using the SecurityWall JWT Analyzer, and explore other focused security assessment tools in the SecurityWall tools section.
JWTs are powerful but require careful evaluation when used in production and security-sensitive contexts. Tooling choices should reflect whether the task is inspection or verification.
Token debuggers and JWT analyzers are complementary, not interchangeable. Understanding their roles and limitations helps engineering and security teams make confident decisions that align with security requirements and threat models.
Tags
About Hisham Mir
Hisham Mir is a cybersecurity professional with 10+ years of hands-on experience and Co-Founder & CTO of SecurityWall. He leads real-world penetration testing and vulnerability research, and is an experienced bug bounty hunter.