How to Read a Nessus Report: Results, Severity & Plugins Explained
Babar Khan Akhunzada
January 2, 2026
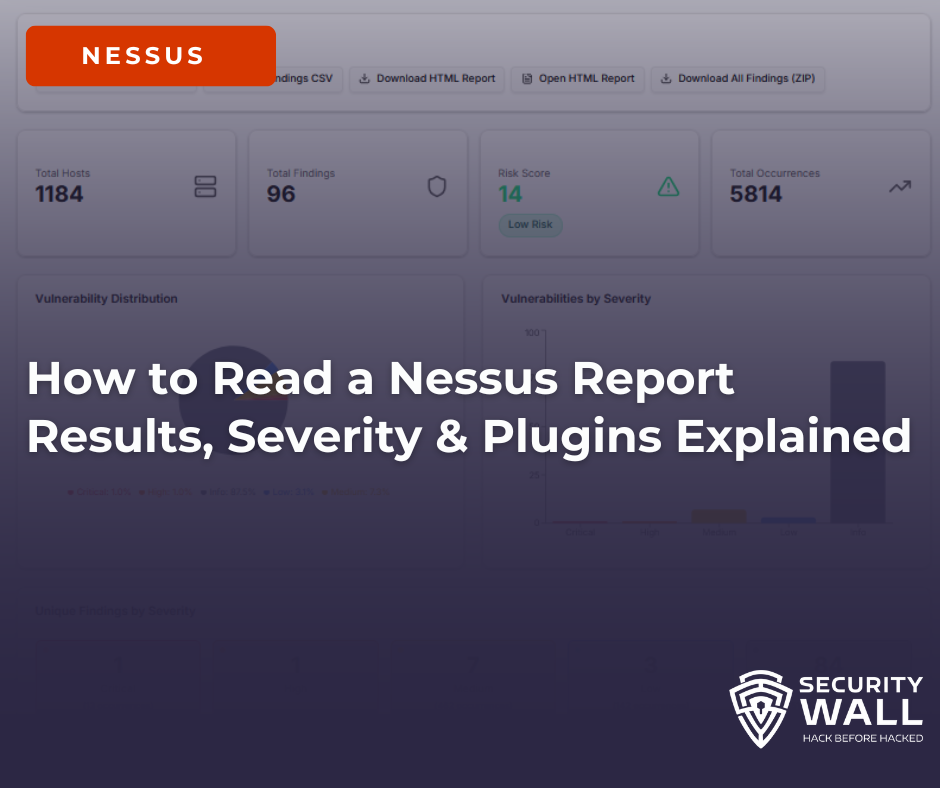
Nessus is one of the most widely used vulnerability scanners for identifying security issues across networks, cloud environments, and applications. While running a scan is straightforward, understanding the Nessus report is where most teams struggle.
Nessus reports are verbose by design. A single scan can generate thousands of findings, many of which are informational, repetitive, or lack business context. This is why searches like how to read a Nessus report and nessus scan results explained continue to grow.
This guide breaks down how Nessus reports work or why they are not , how to interpret severity and plugin IDs correctly, and how to extract meaningful risk insights from Nessus scan results.
What a Nessus Report Contains
A Nessus scan output typically includes:
- Discovered hosts and IP addresses
- Open ports and detected services
- Vulnerability findings tied to plugin IDs
- Severity levels (Critical, High, Medium, Low, Info)
- CVSS scores and CVE references (when available)
When exported as CSV or XML, these findings appear as flat rows, often repeated across multiple hosts and services. This structure makes it difficult to answer basic questions like:
- Which host is most at risk?
- Which vulnerabilities should be fixed first?
- Which findings are just noise?
Understanding Nessus Severity Levels (And Their Limitations)
Nessus assigns severity based primarily on CVSS scoring and plugin logic, not business context.
Severity levels are defined as:
- Critical – Known exploits or high-impact vulnerabilities
- High – Serious issues that may require specific conditions
- Medium – Configuration weaknesses or partial exposure
- Low – Minor risks or difficult-to-exploit findings
- Info – Discovery data, not vulnerabilities
Why severity alone is misleading
A Critical vulnerability on an internal, non-production system may pose less real risk than a Medium issue on an internet-facing application. Nessus does not understand asset value, exposure, or business impact, which is why severity ≠ priority.
This is a common reason vulnerability teams misinterpret Nessus results during vulnerability assessment reviews.
Hosts, Ports, and Services: Where Real Risk Lives
Every Nessus finding is tied to a specific host, port, and service. This context matters more than the vulnerability name itself.
For example:
- An outdated TLS configuration on port 443 of a public web server
- An exposed RDP service on port 3389
- SSH running with weak settings on an internal jump box
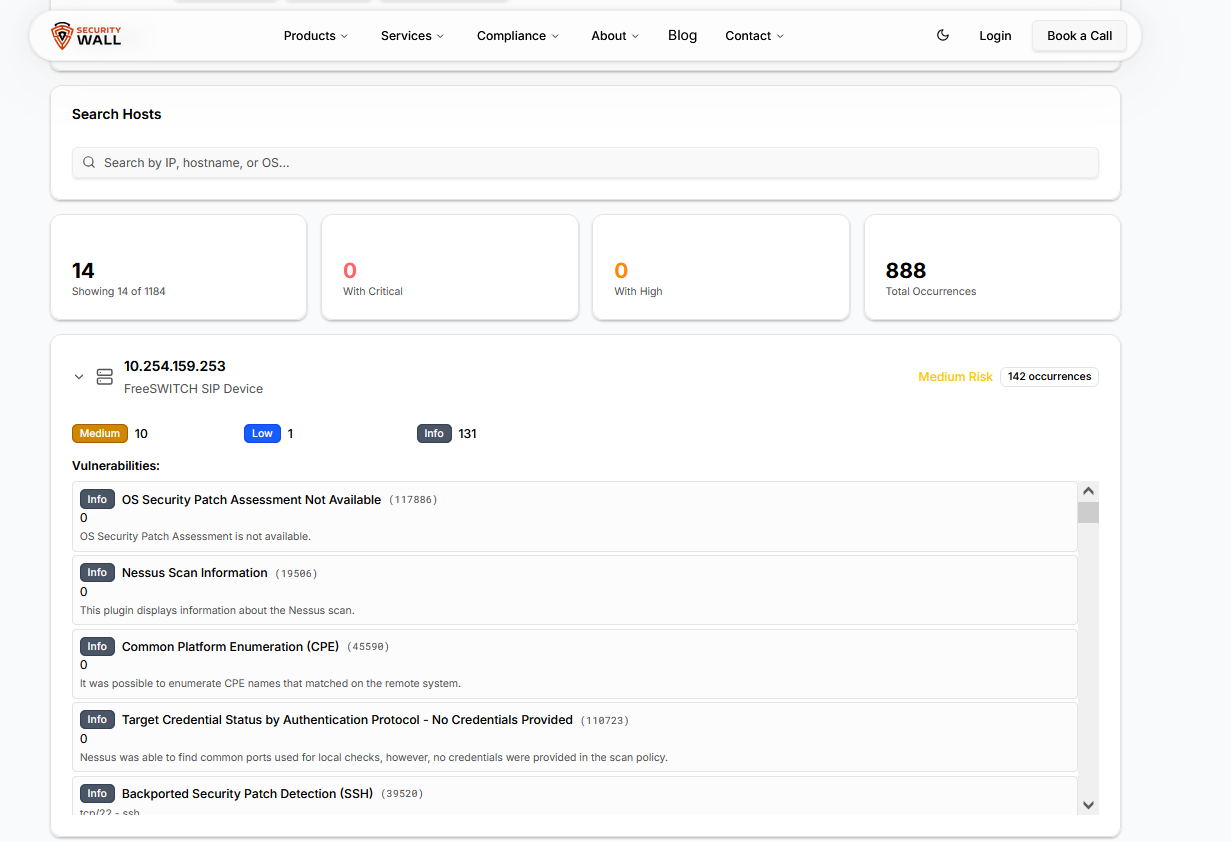
The same vulnerability can have very different risk implications depending on exposure and environment. This is why raw Nessus output often needs validation and contextualization during penetration testing engagements.
Nessus Plugin IDs Explained (What Matters vs Noise)
Each Nessus finding is generated by a plugin ID, which defines how the vulnerability was detected.
Common issues with plugin-based reporting:
- The same plugin ID appears across dozens or hundreds of hosts
- Many plugins are purely informational (scan metadata, OS detection)
- Plugin output may indicate potential issues, not confirmed exploits
When users search for nessus plugin ids explained, they are usually trying to determine which findings require action and which can be ignored. Nessus does not prioritize findings across assets, which leads to alert fatigue and misaligned remediation efforts.
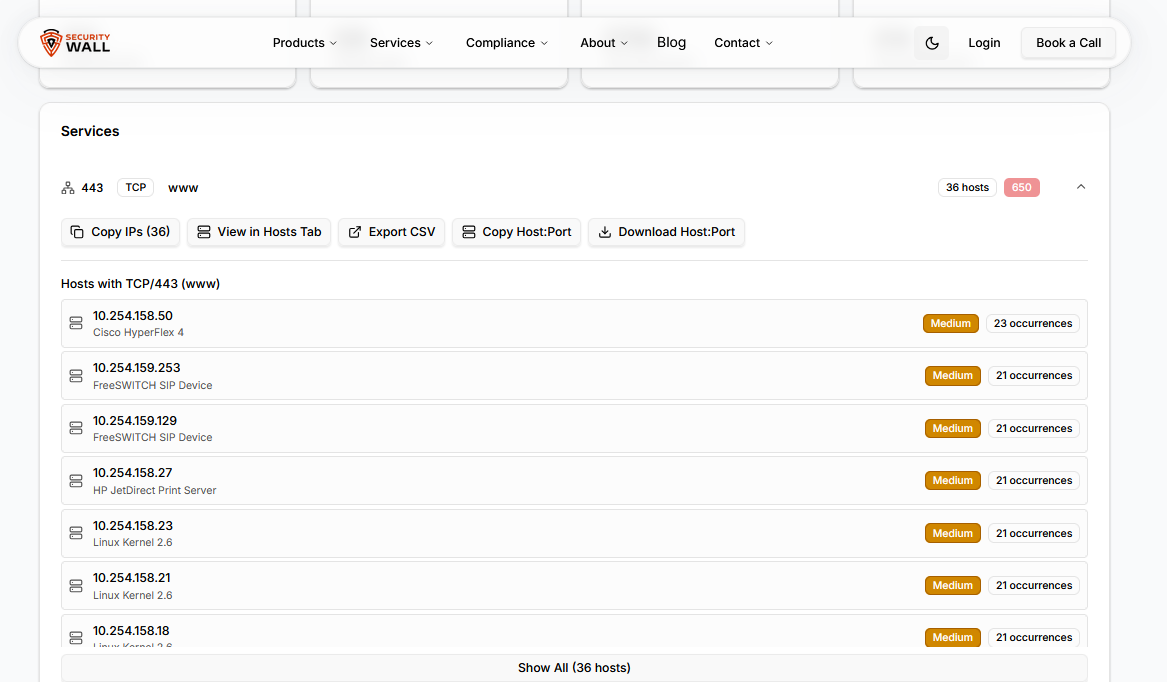
Why Nessus CSV and XML Reports Are Hard to Analyze
Exporting Nessus reports to CSV or XML is common, but these formats introduce major usability problems:
- Thousands of ungrouped rows with no asset-level prioritization
- Repeated plugin IDs inflating report size
- Missing or inconsistent hostnames, especially in cloud scans
- No clear visibility into high-risk hosts or exposed services
This is why many teams struggle with nessus csv report and nessus xml report analysis and resort to manual spreadsheet filtering.
Visualizing Nessus Scan Results for Faster Decisions
To overcome these limitations, many teams choose to visualize Nessus reports instead of reading raw exports.
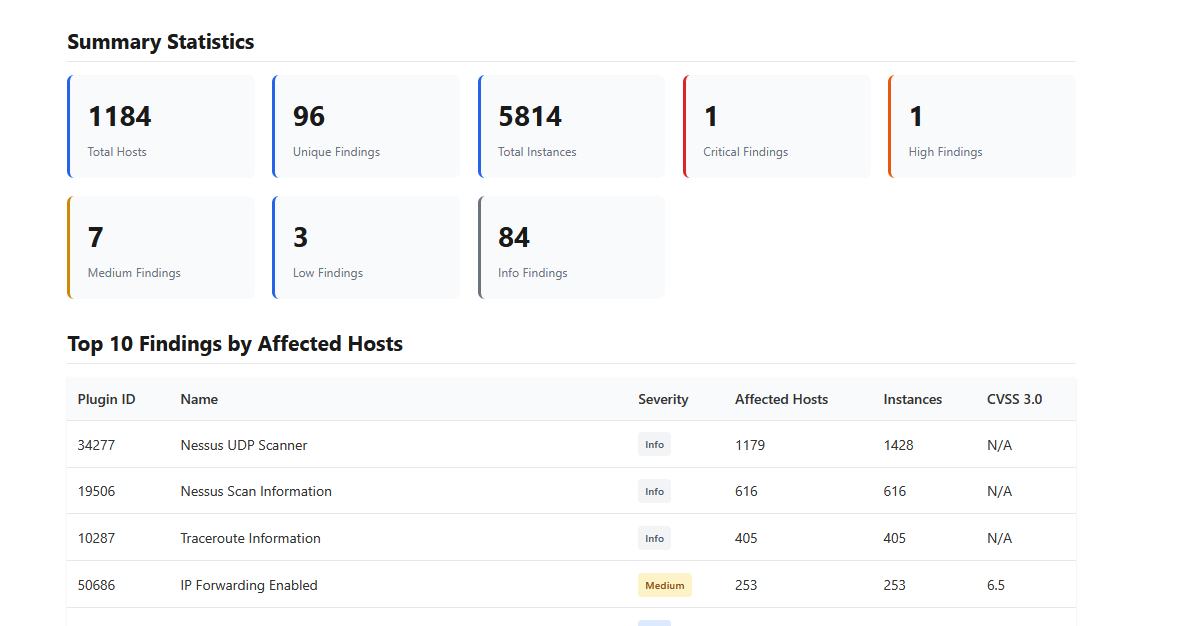
A Nessus report visualizer helps by:
- Grouping vulnerabilities by host, service, and severity
- Highlighting the most vulnerable assets first
- Reducing noise from informational plugins
- Making scan results understandable for both technical and non-technical stakeholders
You can analyze your scan results using the Nessus report visualizer, which converts Nessus XML and CSV files into clear, structured insights.
If you want to understand how this works in practice, this guide explains the process step by step:
Free Nessus Report Visualizer: Instantly Understand Your Nessus Scans
Turning Nessus Findings into Actionable Security Outcomes
Nessus is a detection engine, not a decision-making tool.
To turn findings into real security improvements, organizations often combine Nessus scans with:
- Structured vulnerability assessment findings to prioritize risk
- Validated penetration testing reports to confirm exploitability
- Continuous security platforms like SLASH to track risk over time
This layered approach ensures vulnerabilities are not just identified, but understood, prioritized, and resolved.
If you’re trying to figure out how to read a Nessus report, the challenge isn’t the scan it’s the interpretation.
Severity levels lack business context, plugin IDs create noise, and CSV/XML formats hide real risk. Visualizing Nessus scan results bridges the gap between detection and remediation, allowing teams to focus on what actually matters.
Understand your Nessus scan in minutes
Try the free Nessus report visualizer.
Tags
About Babar Khan Akhunzada
Babar Khan Akhunzada is Founder of SecurityWall. He leads security strategy, offensive operations. Babar has been featured in 25-Under-25 and has been to BlackHat, OWASP, BSides premiere conferences as a speaker.