Your All-in-One
Security Companion
Empowering Security for Modern Businesses Worldwide
From fintech innovators to SaaS platforms, companies rely on SecurityWall to secure their digital assets.





End-to-End Cybersecurity,
Engineered for Modern Businesses
From continuous pentesting to rapid incident response, SecurityWall protects your infrastructure, data, and reputation.
Enterprise Security
Redefined
Discover our flagship security platforms designed to transform your cybersecurity operations with intelligent automation and comprehensive threat protection.
SLASH
Next-Generation Security Orchestration
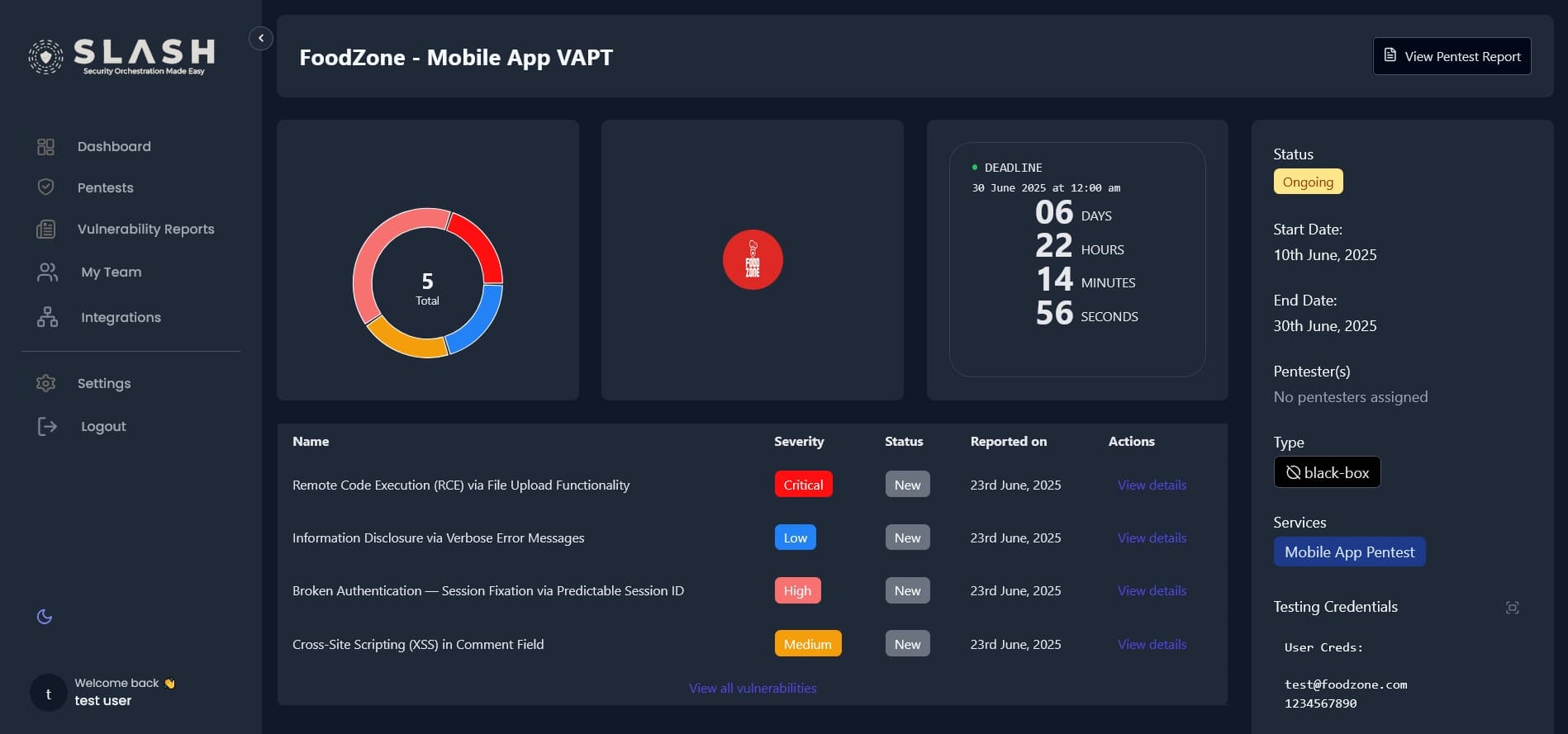
SLASH is a next-generation security orchestration framework engineered to unify vulnerability intelligence, testing operations, and remediation workflows under a single adaptive architecture. It enables seamless coordination between offensive and defensive functions transforming fragmented security processes into a continuous, intelligence-driven cycle of detection, validation, and response.
Operational Metrics
VIGIX
Vigilant Investigation Group for Internet eXposure
VIGIX is an advanced Attack Surface & Threat Intelligence platform that provides continuous visibility into your digital footprint. It monitors exposed assets, vulnerabilities, and external threats empowering you to identify risks before attackers do.
Core Capabilities:
Gain a real-time map of your external exposure. Prioritize the risks that matter most and act before they escalate.
Verified Security Assessments
Every security assessment comes with a blockchain-verified certificate. Build trust with stakeholders through transparent, verifiable security testing.
Blockchain-Verified
Every certificate is tamper-proof and cryptographically signed
24/7 Verification
Anyone can verify certificate authenticity anytime, anywhere
QR Code Access
Instant mobile verification with embedded QR codes
Professional Format
Stakeholder-ready certificates with comprehensive details
Every Assessment Certified
Verifiable by anyone, anytime